Gateway endpoints are the local and remote gateways that are connected by a BOVPN. The gateway endpoints configuration enables your Firebox to specify how to identify and communicate with the remote endpoint device when it negotiates the BOVPN. It also enables the device to specify how to identify itself to the remote endpoint when it negotiates the BOVPN. You must configure at least one gateway endpoint pair when you add a BOVPN virtual interface.
You can configure multiple gateway endpoints for VPN failover. For more information, go toe Configure Branch Office VPN (BOVPN) Failover.
You can specify different pre-shared keys for each gateway endpoint of a virtual interface. For an example of a configuration with different pre-shared keys, go to BOVPN Virtual Interface for Static Routing to Amazon Web Services (AWS).
In Fireware v12.2 or higher, you can specify a secondary interface IP address as a gateway endpoint. By default, the primary IP address configured on the external interface you specify is used.
In Fireware v12.1.x or lower, do not use a secondary interface IP address as a gateway endpoint. If you configure a gateway endpoint with a secondary interface IP address, the BOVPN connection might fail if the local Firebox initiates the BOVPN connection. This is because the Firebox initiates the connection with the primary interface IP address. If the remote endpoint initiates the BOVPN connection and specifies the secondary interface IP address, the connection succeeds.
Local Gateway
In the Local Gateway settings, you configure the gateway ID and the interface the BOVPN connects to on your Firebox. You can configure a BOVPN virtual interface to use any internal or external interface as the local gateway.
For the gateway ID, if you have a static IP address you can select By IP Address. If you have a domain that resolves to the IP address the BOVPN connects to on your Firebox, select By Domain Information.
- Select VPN > BOVPN Virtual Interface.
- Click Add.
- In the Gateway Endpoint section, click Add.
The Gateway Endpoint Settings dialog box appears.
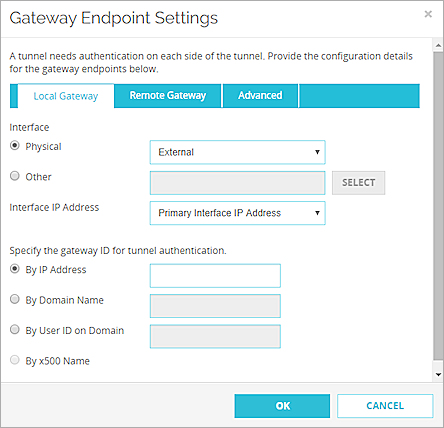
- Select the device physical or logical interface that has the IP address or domain you specified as the gateway ID.
- To select a physical or wireless interface, from the Physical drop-down list, select a configured physical or wireless interface.
- To select a VLAN, Bridge, Link Aggregation, or PPPoE interface:
- Select Other.
- Click Select.
The Select the interface for the local gateway dialog box appears.
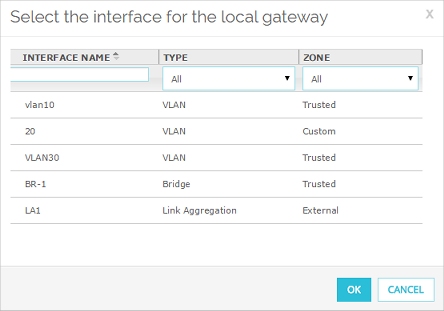
- From the list of interfaces, select the interface.
- To filter the interface list, from the Zone and Name drop-down lists, select an option.
Or, type an interface name in the Name text box.
- (Fireware v12.2 or higher) In the Interface IP Address drop-down list, select Primary Interface IP Address or select a secondary IP address that is already configured on the selected external interface. Tip!
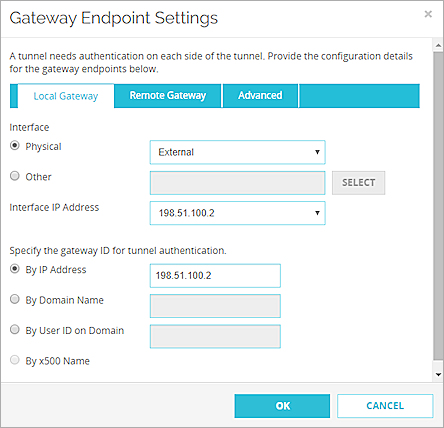
- Select an option and specify the gateway ID:
- By IP address — Type the IP address of the Firebox interface.
In Fireware v12.1.1 or lower, do not specify a secondary interface IP address as the gateway ID. - By Domain Name — Type your domain name. In Fireware v12.5.2 or higher, you can specify up to 255 characters. In Fireware v12.5.1 or lower, you must specify 63 characters or fewer.
- By User ID on Domain — Type the user name and domain with the UserName@DomainName format . In Fireware v12.5.2 or higher, you can specify up to 255 characters. In Fireware v12.5.1 or lower, you must specify 63 characters or fewer.
- By x500 Name — This option is automatically selected if you specified a certificate as the credential method. In Fireware v12.5.2 or higher, you can specify a certificate with an x500 name up to 255 characters in length. In Fireware v12.5.1 or lower, you must specify 63 characters or fewer.
- By IP address — Type the IP address of the Firebox interface.
- Select VPN > BOVPN Virtual Interfaces.
The New BOVPN Virtual Interface dialog box appears. - In the Gateway Endpoints section, click Add.
The New Gateway Endpoints Settings dialog box appears.
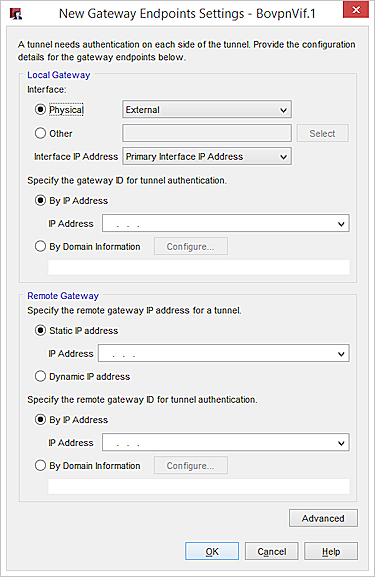
- Select the device physical or logical interface that has the IP address or domain you specified as the gateway ID.
- To select a physical or wireless interface, from the Physical drop-down list, select a configured physical or wireless interface.
- To select a VLAN, Bridge, Link Aggregation or PPPoE interface:
- Select Other.
- Click Select.
The Configure Local Interface for Gateway Endpoint dialog box appears.
- From the list of interfaces, select the interface.
- To filter the interface list, from the Zone and Name drop-down lists, select an option.
Or, type an interface name in the Name text box.
- (Fireware v12.2 or higher) In the Interface IP Address drop-down list, select Primary Interface IP Address or select a secondary IP address that is already configured on the selected external interface. Tip!

- Select an option and specify the gateway ID:
- By IP address — Type or select the IP address of the Firebox interface.
In Fireware v12.1.1 or lower, do not specify a secondary interface IP address as the gateway ID. - By Domain Information — Click Configure and select the domain configuration method:
- By Domain Name — Type your domain name and click OK. In Fireware v12.5.2 or higher, you can specify up to 255 characters. In Fireware v12.5.1 or lower, you must specify 63 characters or fewer.
- By User ID on Domain — Type the user name and domain with the UserName@DomainName format and click OK. In Fireware v12.5.2 or higher, you can specify up to 255 characters. In Fireware v12.5.1 or lower, you must specify 63 characters or fewer.
- By IP address — Type or select the IP address of the Firebox interface.
Remote Gateway
If the remote VPN endpoint gets an external IP address from DHCP or PPPoE, set the ID type of the remote gateway to Domain Name. Set the peer name to the fully qualified domain name of the remote VPN endpoint. The Firebox uses the IP address and domain name to find the VPN endpoint. Make sure the DNS server the device uses can identify the name.
- In the Gateway Endpoint Settings dialog box, select the Remote Gateway tab.

- Select the remote gateway IP address type:
- Static IP address — Select this option if the remote device has a static IP address. Type or select the IP address.
In Fireware v12.4 or higher, you must specify an IP address type that matches the Address Family setting you configured earlier. For example, if you specified IPv6 Addresses, you must specify an IPv6 address in the Static IP address text box. - Dynamic IP address — Select this option if the remote device has a dynamic IP address.
- Static IP address — Select this option if the remote device has a static IP address. Type or select the IP address.
- Select an option and specify the remote gateway ID:
- By IP address — Type the IP address.
In Fireware v12.4 or higher, you must specify an IP address type that matches the Address Family setting you configured earlier. For example, if you specified IPv6 Addresses, you must specify an IPv6 address in the By IP address text box. - By Domain Name — Type the domain name. In Fireware v12.5.2 or higher, you can specify up to 255 characters. In Fireware v12.5.1 or lower, you must specify 63 characters or fewer.
- By User ID on Domain — Type the user ID and domain. In Fireware v12.5.2 or higher, you can specify up to 255 characters. In Fireware v12.5.1 or lower, you must specify 63 characters or fewer.
- By x500 Name — Type the x500 name. In Fireware v12.5.2 or higher, you can specify up to 255 characters. In Fireware v12.5.1 or lower, you must specify 63 characters or fewer.
For an IPv4 gateway endpoint, if the domain name of the remote endpoint can be resolved, select the Attempt to resolve domain check box.
When this option is selected, the device automatically does a DNS query to find the IP address associated with the domain name for the remote endpoint. Connections do not proceed until the domain name can be resolved. Select this check box for configurations that depend on a dynamic DNS server to maintain a mapping between a dynamic IP address and a domain name. - By IP address — Type the IP address.
- Click OK.
The gateway pair you defined appears in the list of gateway endpoints. - To configure Phase 1 settings for this gateway, follow the steps in Configure IPSec VPN Phase 1 Settings.
- Select the remote gateway IP address type:
- Static IP address — Select this option if the remote device has a static IP address. Type or select the IP address.
In Fireware v12.4 or higher, you must specify an IP address type that matches the Address Family setting you configured earlier. For example, if you specified IPv6 Addresses, you must specify an IPv6 address in the Static IP address text box. - Dynamic IP address — Select this option if the remote device has a dynamic IP address.
- Static IP address — Select this option if the remote device has a static IP address. Type or select the IP address.
- Select an option and specify the gateway ID:
- By IP address — Type the IP address or select it from the drop-down list.
In Fireware v12.4 or higher, you must specify an IP address type that matches the Address Family setting you configured earlier. For example, if you specified IPv6 Addresses, you must specify an IPv6 address in the By IP address text box. - By Domain Information
- Click Configure and select the method of domain configuration: Domain Name, User ID @ Domain, or X500 Name.
- Type the name, user ID and domain, or x500 name. In Fireware v12.5.2 or higher, you can specify up to 255 characters. In Fireware v12.5.1 or lower, you must specify 63 characters or fewer.
- For an IPv4 gateway endpoint, if the domain name of the remote endpoint can be resolved, select the Attempt to resolve check box.
When this option is selected, the device automatically does a DNS query to find the IP address associated with the domain name for the remote endpoint. Connections do not proceed until the domain name can be resolved. Select this check box for configurations that depend on a dynamic DNS server to maintain a mapping between a dynamic IP address and a domain name. - Click OK.
- By IP address — Type the IP address or select it from the drop-down list.

- Click OK to close the New Gateway Endpoints Settings dialog box.
The gateway pair you defined appears in the list of gateway endpoints. - To use Phase 1 settings other than the default values, follow the steps in Configure IPSec VPN Phase 1 Settings. Otherwise, click OK.
Advanced Settings
CA Certificate
(Fireware v12.6.2 or higher) This option appears if you select a certificate for authentication. When you enable this option, you must select a root or intermediate CA certificate from the CA Certificate drop-down list. The Firebox uses that CA certificate to verify the certificate received from VPN peer. The certificate from the VPN peer must be part of the certificate chain that includes the specified root or intermediate CA certificate. If the peer certificate is not part of the chain, the Firebox rejects Phase 1 tunnel negotiations.

Different pre-shared key
You can specify different pre-shared keys for each gateway endpoint. You might select this option if you configure a VPN between a Firebox and third-party endpoint, and the third-party endpoint requires each gateway endpoint to have a different pre-shared key.
(Fireware v12.5.4 or higher) Select String-Based or Hex-Based. The default setting is String-Based. For information about hex-based keys, go to Hex-Based Pre-Shared Keys.
DF Bit
The Don't Fragment (DF) bit is a flag in the header of a packet. You can select Copy, Set, or Clear to control whether the Firebox uses the original DF bit setting in the packet header:

The DF bit setting in Fireware Web UI

The DF bit setting in Policy Manager
- Copy — This option applies the DF bit setting of the original frame to the IPSec encrypted packet.
If a frame does not have the DF bits set, the Firebox does not set the DF bits and fragments the packet if needed. If a frame is set to not be fragmented, the Firebox encapsulates the entire frame and sets the DF bits of the encrypted packet to match the original frame. - Set — This option instructs the Firebox to not fragment the frame regardless of the original bit setting.
If a user must make IPSec connections to a Firebox from behind a different Firebox, you must clear this check box to enable the IPSec pass-through feature. For example, if mobile employees are at a customer location that has a Firebox, they can make IPSec connections to their network with IPSec. For your local Firebox to correctly allow the outgoing IPSec connection, you must also add an IPSec policy. - Clear — This option breaks the frame into pieces that can fit in an IPSec packet with the ESP or AH header, regardless of the original bit setting.
In Fireware v12.2 or lower, you can only configure the DF Bit setting in the external interface settings.
In Fireware v12.2.1 or higher, you can configure the DF Bit setting in the BOVPN gateway endpoint settings. This setting takes effect immediately. The DF Bit setting specified for the gateway endpoint overrides the DF Bit setting specified for the external interface.
If you do not specify a DF Bit setting for the gateway endpoint, the gateway endpoint uses the DF Bit setting specified in the external interface settings. For more information about the DF Bit setting in the external interface settings, go to Define Gateway Endpoints for a BOVPN Gateway.
PMTU
The Path Maximum Transmission Unit (PMTU) setting controls the length of time that the Firebox lowers the MTU for an IPSec VPN tunnel when it gets an ICMP Request to Fragment packet from a router with a lower MTU setting on the Internet.
In Fireware v12.2.1 or higher, you can configure PMTU settings in the BOVPN gateway endpoint settings. The PMTU settings specified for the gateway endpoint override the PMTU settings specified for the external interface. If you do not specify PMTU settings for a gateway endpoint, the gateway endpoint uses the PMTU settings specified in the external interface settings.
We recommend that you keep the default setting. This can protect you from a router on the Internet with a very low MTU setting.

The PMTU bit setting in Fireware Web UI
The PMTU bit setting in Policy Manager