Applies To: Cloud-managed Fireboxes
You can add and manage an active/passive cloud-managed FireCluster in WatchGuard Cloud.
- If you have two cloud-managed Fireboxes that you have not yet configured as a FireCluster, use the method described in this section.
- Both Fireboxes must have factory-default settings.
Before you add a cloud-managed FireCluster, learn about the requirements and plan your configuration. For more information, go to Before You Configure a Cloud-Managed FireCluster in WatchGuard Cloud.
- Reset both Fireboxes to factory-default settings. For more information, go to Reset a Firebox.
- Log in to your WatchGuard Cloud Subscriber account.
- Select Configure > Devices.
- Click Add Device.
A list of activated devices appears. If the list does not include your devices, review the requirements in Before You Configure a Cloud-Managed FireCluster in WatchGuard Cloud.

- Click Add FireCluster.
The selection page for the first FireCluster member opens.

- To add the first FireCluster member, click a Firebox name.
The selection page for the second FireCluster member opens.
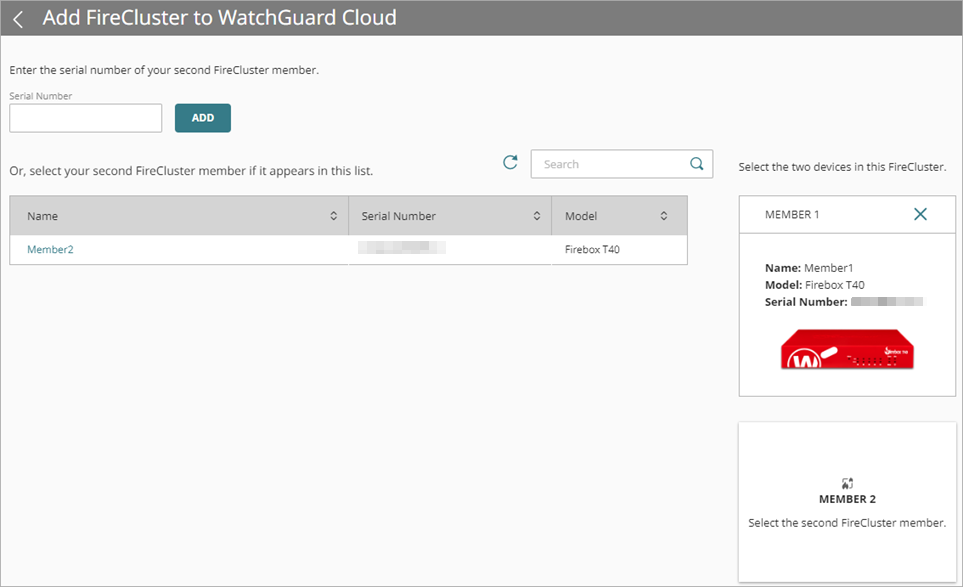
- To add the second FireCluster member, do one of the following:
- Enter the serial number of the second FireCluster member and click Add.
- From the list of devices, click a Firebox name.
Selected FireCluster members appear next to the device list.
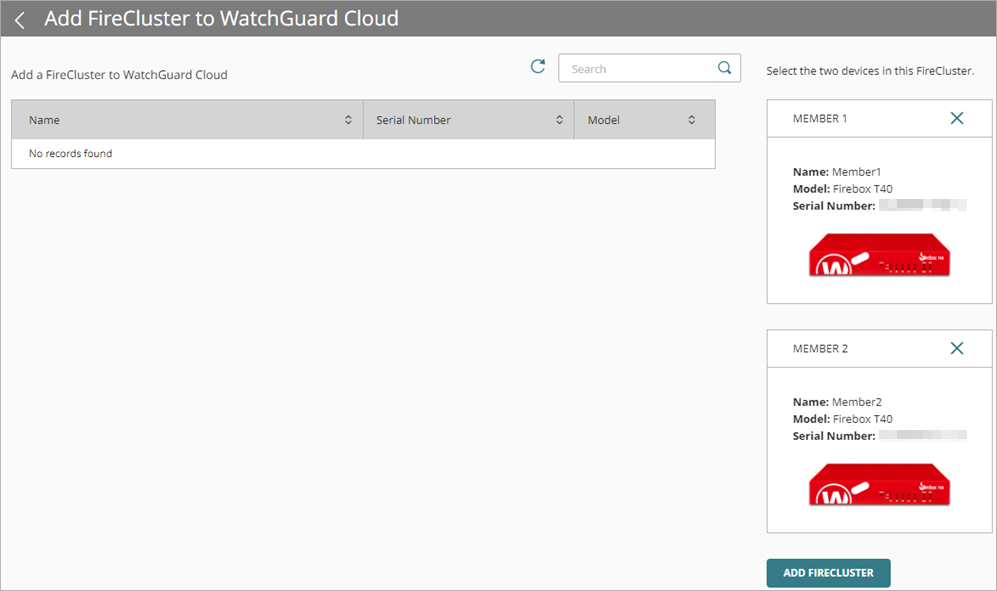
- Click Add FireCluster.
A confirmation page opens.
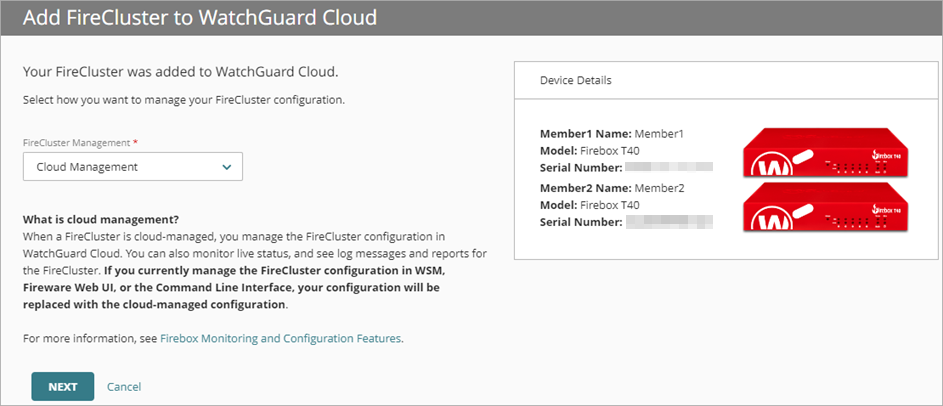
- From the FireCluster Management drop-down list, click Cloud Management.
- Click Next.
- Enter the FireCluster Name.
- Enter the Member1 Name.
- Enter the Member2 Name.
- Select a Time Zone. The time zone settings control the date and time that appear in the log messages and reports for your FireCluster.
- Select the device folder for your Firebox. Device Folders help you to see status and summary data for device groups.
If you only have one root folder, the folder list does not appear. - Click Next.
- From the Cluster Interface drop-down list, select an interface.
Cluster members use this dedicated interface to exchange heartbeat packets and to synchronize connection and session information. - In the Member1 Cluster IP Address and Member2 Cluster IP Address text boxes, enter an IP address that is not in use on your network.
To avoid conflicts with routable IP addresses, we recommend APIPA addresses or IP addresses from a dedicated private subnet. - In the Cluster ID text box, enter a number between 1 and 255. The default cluster ID is 50.
The Cluster ID determines the virtual MAC (VMAC) addresses that cluster member interfaces use. If there is another FireCluster or any devices that use the VRRP protocol on the same subnet, enter a Cluster ID that is different from the Cluster ID of another FireCluster to avoid a virtual MAC address conflict. For information about how the VMAC address is calculated, go to Active/Passive Cluster ID and the Virtual MAC Address.

- (Optional) To add redundancy, select Assign Backup Cluster Interface. The FireCluster uses the backup cluster interface if the primary cluster interface fails. We recommend this option for FireCluster configurations without a direct cable connection between cluster members. For more information about this setting, go to Before You Configure a Cloud-Managed FireCluster in WatchGuard Cloud.
- From the Backup Cluster Interface drop-down list, select an interface.
- In the Member1 Cluster Backup IP Address and Member2 Cluster Backup IP Address text boxes, enter an IP address that is not in use on your network. To avoid conflicts with routable IP addresses, we recommend APIPA addresses or IP addresses from a dedicated private subnet.
The primary and backup cluster interfaces must be on different subnets. We recommend that you do not use a switch between each member for the cluster interfaces. If you do use a switch between cluster interfaces, the cluster interfaces must be logically separated from each other on different VLANs. We recommend that you configure a backup cluster interface if you separate the cluster interfaces with a switch.

- Click Next.
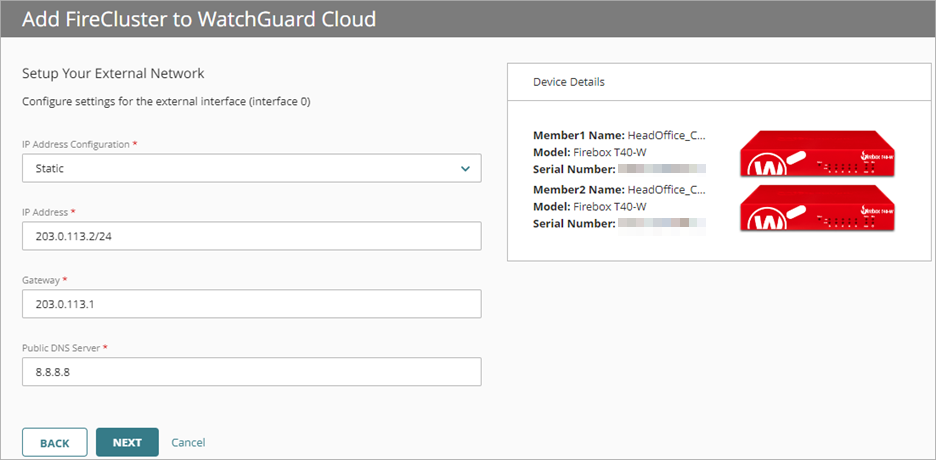
- From the IP Address Configuration drop-down list, select Static, DHCP, or PPPoE.
- If you selected Static:
- In the IP Address text box, enter an IP address for the external interface.
- In the Gateway text box, enter an IP address for the gateway.
- In the Public DNS Server text box, enter the IP address of a public DNS server for name resolution.
- If you selected DHCP or PPPoE:
- Select Obtain an IP address automatically or Use this IP address.
- Enter the Client Name.
- Enter the Host Name.
- If you selected Use this IP address, enter an IP address.
- Click Next.
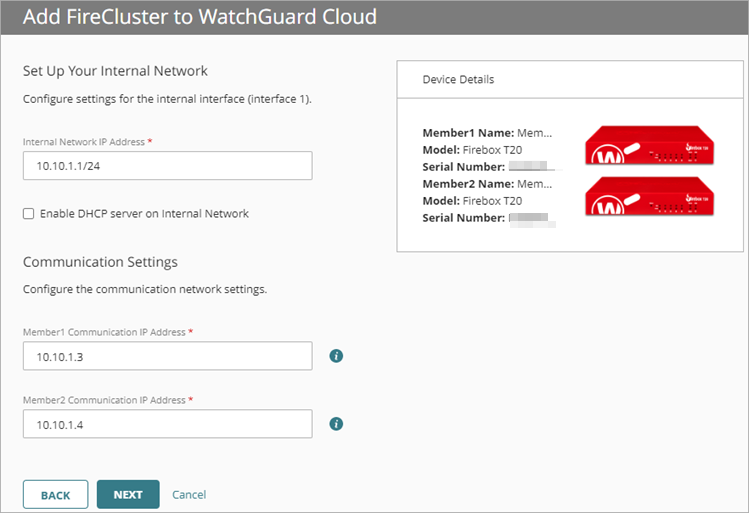
- Enter the Internal Network IP Address.
- (Optional) Select Enable DHCP server on Internal Network.
- Enter a Starting IP Address.
- Enter an Ending IP Address.
- In the Member1 Communication IP Address text box, type an IP address that is on the same subnet as your internal network. Your Dimension or syslog server must also be on this network.
- In the Member2 Communication IP Address text box, type an IP address that is on the same subnet as your internal network. Your Dimension or syslog server must also be on this network.
- Click Next.
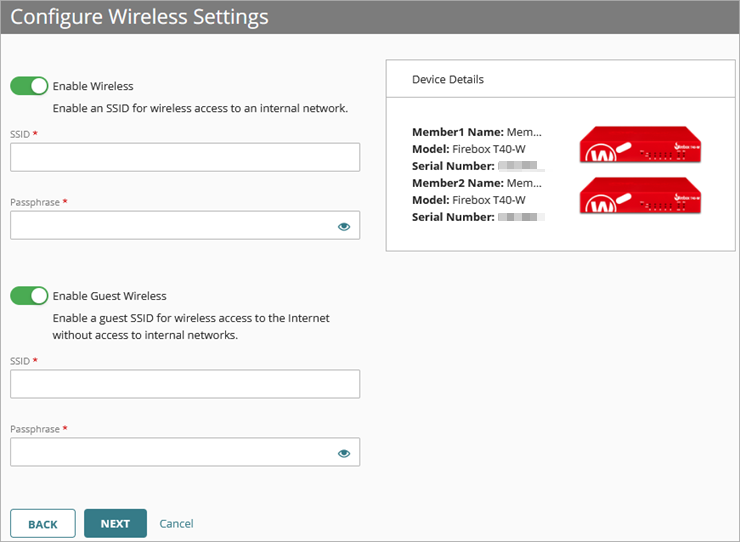
- (Optional) If your Firebox is a wireless model, on the Configure Wireless Settings page, you can enable these options:
- Enable Wireless — If you enable this option, enter the SSID and Passphrase for your internal wireless network.
- Enable Guest Wireless — If you enable this option, enter the SSID and Passphrase for your guest wireless network.
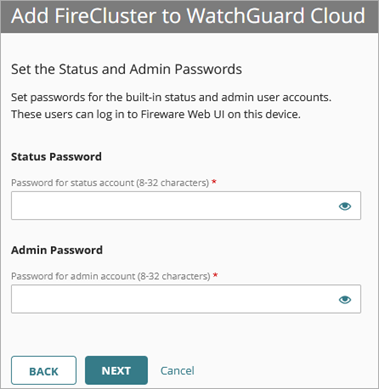
- Enter a Status Password.
- Enter an Admin Password. This password must be different than the status password.
- To complete the configuration and change to cloud management, click OK.
The configuration change deploys automatically.
If you selected the static IP address option, before you click Done:
- Follow the instructions on the Connect Your FireCluster page.
- To use a USB drive, you must click Download the connection settings file on the Connect Your FireCluster page now. You cannot return to this page later.

To connect two Fireboxes in a cloud-managed FireCluster configuration:
- Use an Ethernet cable to connect the cluster interface on one Firebox to the cluster interface on the other Firebox. You can use a straight or crossover cable.
- (Optional) Use a second Ethernet cable to connect the backup cluster interfaces.
- Connect the external interface of each Firebox to a network switch or VLAN. If you use Multi-WAN, connect the second external interface of each Firebox to another network switch.
- Connect the trusted interface of each device to an internal network switch or VLAN.
- For each Firebox, connect the other trusted or optional network interfaces to the internal network switch for that Firebox.
We recommend that you do not use a switch between each member for the cluster interfaces. If you do use a switch between cluster interfaces, the cluster interfaces must be logically separated from each other on different VLANs.
You must connect each pair of network interfaces to a separate local network or VLAN.
WARNING: If any interface on the Firebox configuration uses the IP address 10.0.1.1, do not connect the trusted and optional network interfaces of the second device to the switches until after the cluster has been formed. This avoids an IP address conflict when you start the second device with factory-default settings. The devices use the cluster interfaces to form the cluster. After the you save the configuration to the cluster master, and the cluster is active, connect each of the trusted and optional interfaces of the second device to the appropriate switches.
This diagram shows connections for a simple cloud-managed FireCluster configuration.

In this example, the FireCluster has one external and one trusted interface connected to network switches. The cluster interfaces are connected by an Ethernet cable.
After you complete the cable configuration, verify the FireCluster connection to WatchGuard Cloud. For more information, go to the Device Summary page.
Only the cluster master connects to WatchGuard Cloud.
- The status of the cluster master is Connected.
- The status of the backup master is Never Connected (has not yet connected to WatchGuard Cloud for the first time), or Not Connected (is not currently connected to WatchGuard Cloud).

About FireCluster in WatchGuard Cloud
Before You Configure a Cloud-Managed FireCluster in WatchGuard Cloud