Applies To: ThreatSync+ NDR
ThreatSync+ NDR uses artificial intelligence (AI) to consolidate data related to a large volume of network traffic into Smart Alerts. Smart Alerts indicate that a potential attack might be in progress on your network and guides operators to focus on emerging threats that pose the greatest risk and organizational impact.
The Smart Alerts page is available with a ThreatSync+ NDR license. For more information, go to About ThreatSync+ NDR Licenses.
When ThreatSync+ NDR detects threats to your network or abnormal network activity, Smart Alerts notify you to review the activity and respond. Smart Alerts explain the activity, how it was found, and why it is considered a threat.
When first detected, Smart Alerts are in a New state. If ThreatSync+ NDR detects additional activity related to the alert, the Smart Alert is moved to an Updated state. After you review and remediate the threat, you can then move the Smart Alert to a Closed state.
When ThreatSync+ NDR generates a Smart Alert, it shows on the Monitor > ThreatSync+ > Smart Alerts page. You can also set up notifications to receive an email when ThreatSync+ NDR generates or updates Smart Alerts. For more information, go to Configure ThreatSync+ Alerts and Notification Rules.
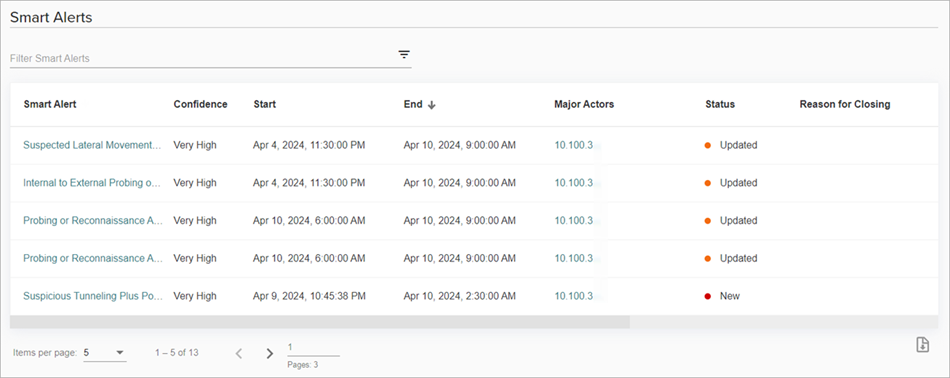
The Smart Alerts page shows a list of Smart Alerts and these details:
- Smart Alert — The name of the Smart Alert.
- Confidence — Indicates how confident ThreatSync+ NDR is that the Smart Alert is a threat. Confidence levels can be Very Low, Low, Medium, High, or Very High.
- Start — The date and time the activity started.
- End — The date and time the activity ended.
- Major Actors — The name, IP address, or email address of the user or entity associated with a device that can carry out malicious activities. Major actors can be the device that is responsible for the threat or the compromised device.
- Status — The status of the Smart Alert. The status can be New, Updated, or Closed.
- Reason for Closing — The reason the Smart Alert was closed by a user.
- Closed By — The name of the user that closed the Smart Alert.
- Closed Similar — Indicates whether the operator requested that future similar Smart Alerts be automatically closed.
- Comments — Shows comments added to the Smart Alert.
Smart Alert Types and Behaviors
The type of Smart Alert and whether it is a Very Low, Low, Medium, High, or Very High threat determines what action to take to protect your network. For example, Exfiltration or Command and Control Smart Alerts might indicate that an attacker is active in your network. Probing and Reconnaissance Smart Alerts might indicate that a new attacker started to attack your network.
We recommend you first address behaviors that occur later in the cyberattack process, such as exfiltration, but it is also important to address the earlier threats because the best way to protect your organization is to catch an attacker early.
A Smart Alert can show multiple malicious behaviors. For example, Suspicious Tunneling plus Port Scan is a combination of two malicious behaviors: a horizontal port scan and a suspicious DNS tunnel.
Smart Alerts types include:
- Internal to External Probing or Reconnaissance Activity
- Suspicious Tunneling Plus Data Exfiltration
- Suspicious DNS Tunneling Plus Port Scan
- Suspicious Tunneling Plus Port Scan
- Suspicious Tunneling Plus Data Exfiltration
- Probing or Reconnaissance Activity
- Suspected Lateral Movement Activity
Smart Alert behaviors include:
- Suspicious Beaconing Behavior Through Web Application Interface
- Internal to External Horizontal Port Scan
- Internal to External Vertical Port Scan
- Peer to Peer Exfiltration
- Horizontal Port Scan
- High Volume Crossing the Network Boundary
- Suspicious DNS Tunneling
- Suspicious ICMP Tunneling
- Large Ephemeral Port Footprint
- Visit Malicious URL or Domain Through Blocklist IP
- Suspicious RDP Tunneling Activity
- Suspicious Activity On an Asset
To view detailed information about a specific Smart Alert, and guidance for remediation, click the Smart Alert. For more information, go to Review Smart Alert Details.