Applies To: ThreatSync+ NDR
Every Smart Alert provides detailed information about the threat, and includes a summary of the Smart Alert and graphs and metrics that show specific activities performed by the major actor. Review open Smart Alerts to determine if the Smart Alert indicates a real threat to your network.
The Smart Alerts and Smart Alerts Details page is available with a ThreatSync+ NDR license. For more information, go to About ThreatSync+ NDR Licenses.
To review Smart Alert details:
- Log in to your WatchGuard Cloud account.
- Select Monitor > ThreatSync+ > Smart Alerts.
The Smart Alerts page opens and shows a list of open Smart Alerts. - Click the Smart Alert you want to review.
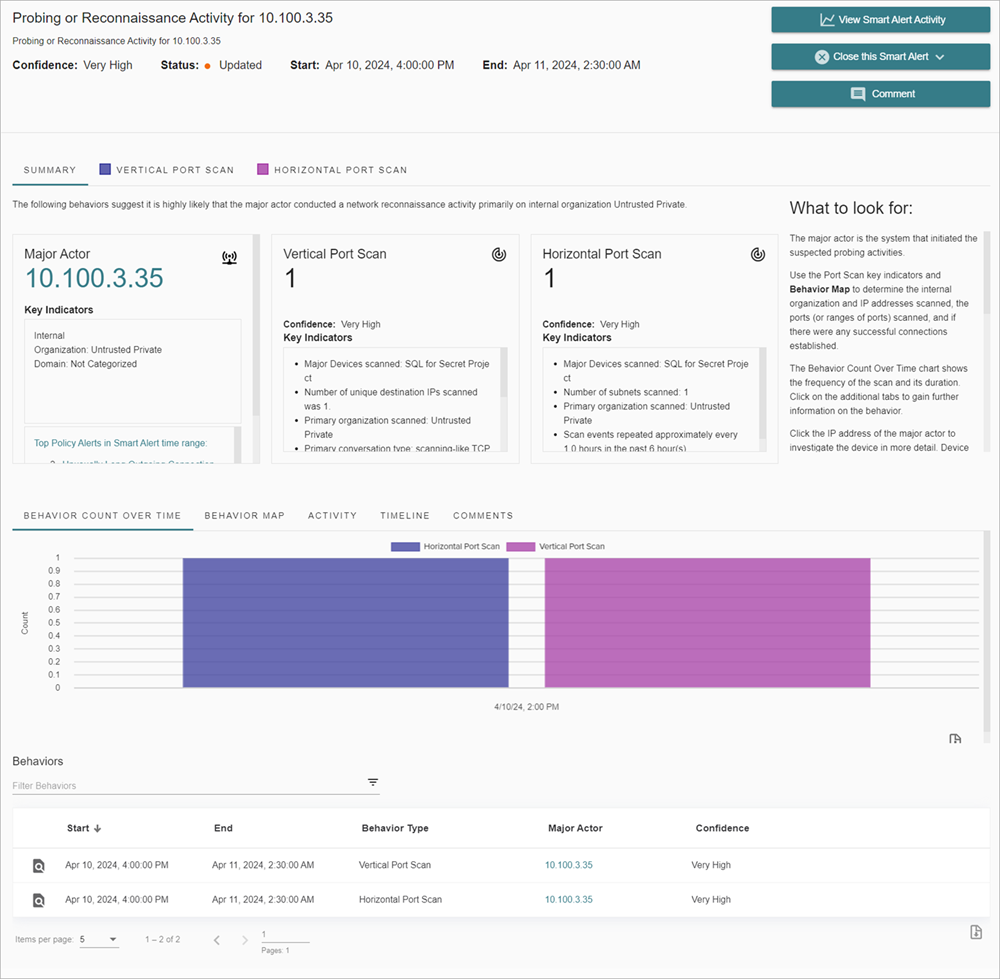
The Smart Alert Details page opens with the Summary tab selected by default.
To learn more about the Smart Alert Details page, go to these sections:
- View Smart Alert Activity
- Summary Tab
- Major Actor
- What To Look For
- Behavior Indicators
- Key Indicators
- Smart Alert Recurrence
- Behavior Charts and Maps
- Behavior Details
- Remediate Smart Alerts
- Close a Smart Alert
View Smart Alert Activity
To view detailed traffic information about the Smart Alert, click View Smart Alert Activity. For more information about traffic investigation, go to Investigate ThreatSync+ Traffic.
Summary Tab
The Summary tab on the Smart Alert details page provides a snapshot of threat activity. The Summary tab includes widgets with summary information about the major actor and the associated activity the major actor performed on your network.
Major Actor
A major actor is the device that is associated with malicious activity. The major actor can be the device that is responsible for the threat, or it might be the compromised device that an attacker uses to carry out the malicious behavior. The Major Actor widget on the Summary tab can include the IP address, key indicators, and a link to related policy alerts. To learn more about the major actor, click the name, email address, or IP address on the Major Actor widget.
For more information about policy alerts, go to About Policy Alerts.
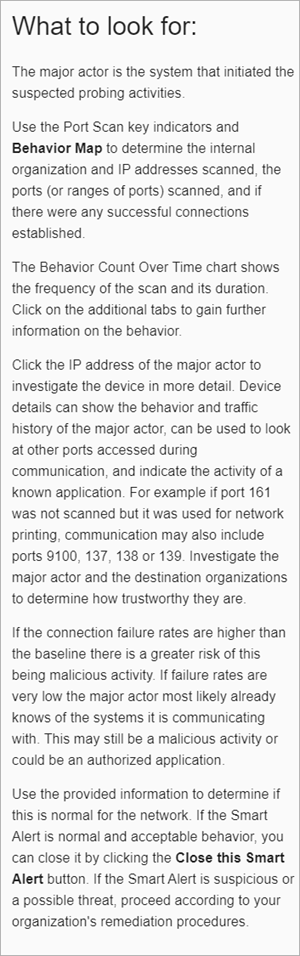
What To Look For
The What to Look For section shows important information about the type of Smart Alert and recommendations about how to review and diagnose the threat. Every Smart Alert shows the What to Look For section on the Summary tab and also on every behavior type tab that describes specific Smart Alert activity. We recommend you start your Smart Alert review with this section to learn more about the type of threat and review the suggestions to remediate.
This example is for a Probing or Reconnaissance Smart Alert:
Behavior Indicators
Behavior indicators represent the type of activity related to the threat generated a Smart Alert. Behavior indicators are included in the Summary tab and also on every behavior type tab for the Smart Alert. All behavior types show information about the major actor and confidence level of the threat.
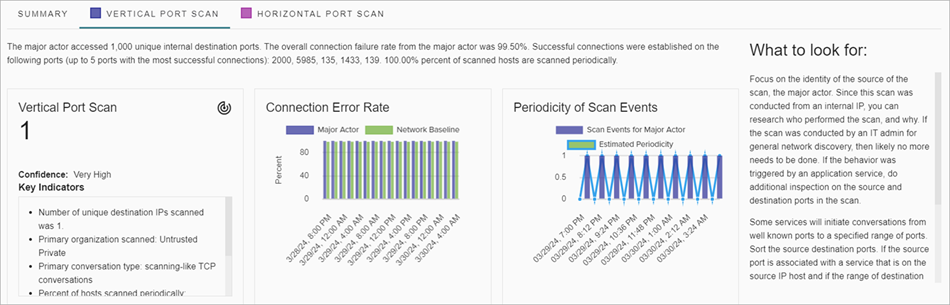
Behavior type tabs vary by Smart Alert type and can include:
- Internal to External Horizontal Port Scan — Shows details about IP addresses the major actor scanned and includes the number of IP addresses scanned, the organization, and details about which port was involved in the scanning activity.
- Suspicious DNS Tunneling — The DNS Traffic Anomalies chart shows anomalies recorded when the major actor sent DNS requests.
- Horizontal Port Scan — Shows details about the subnets and organizations scanned and includes metrics about the connection error rate and ICMP requests.
- Vertical Port Scan — Shows details about ports connected to on a single destination IP address and includes metrics about the connection error rate and scan events.
- High Volume Data Transfer From Inbound to Outbound — Shows details about suspicious network traffic that leaves your network, and includes primary destination organization by traffic volume, total traffic volume, affected ports, and the total number of flows with high volume to external systems.
Key Indicators
Key indicators provide you with more details about the behaviors detected and show on every widget on the Summary tab and also on every behavior type tab. Details can include the organization involved, domain, network traffic details, and threat details.
Smart Alert Recurrence
An alert that recurs frequently might simply be activity from an approved application on your network that probes or communicates in a way that looks suspicious. Many application clients perform server scanning that looks similar to malicious port scans. Some applications perform automated, regular communications with cloud services such as GitHub that could look like Command and Control tunneling activity.
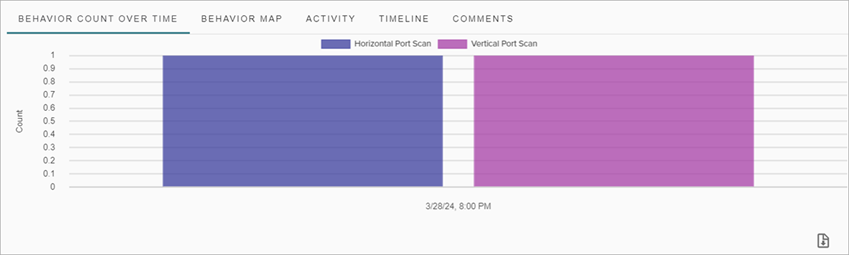
Behavior Charts and Maps
Smart Alert details include several charts and maps and provide details about the behavior by time, historical activity, and timeline.
- Behavior Count Over Time — Shows the behavior types associated with the Smart Alert, the frequency of the scan, and how long the scan took.
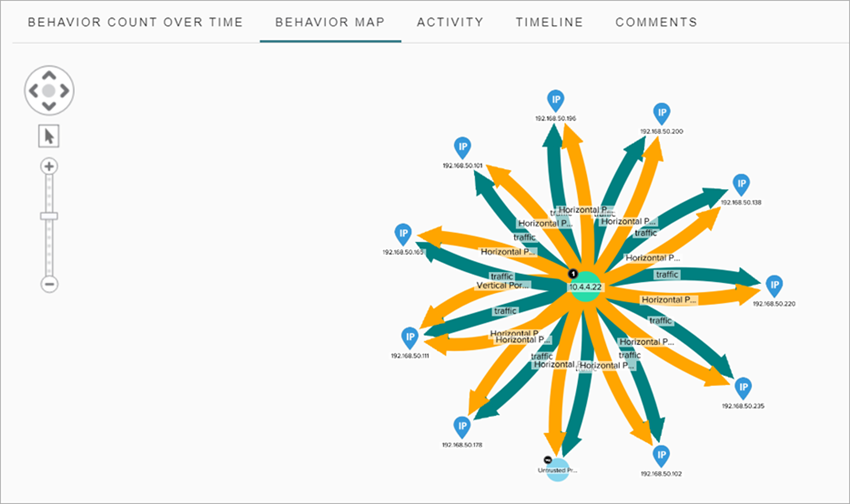
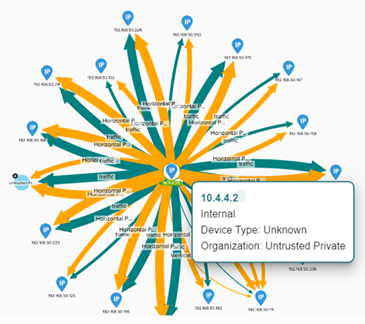
- Behavior Map — Shows details about the links between the major actor and the different behavior types. You can point to each behavior type and IP address to view details about the device type, organization, or location of the behavior.
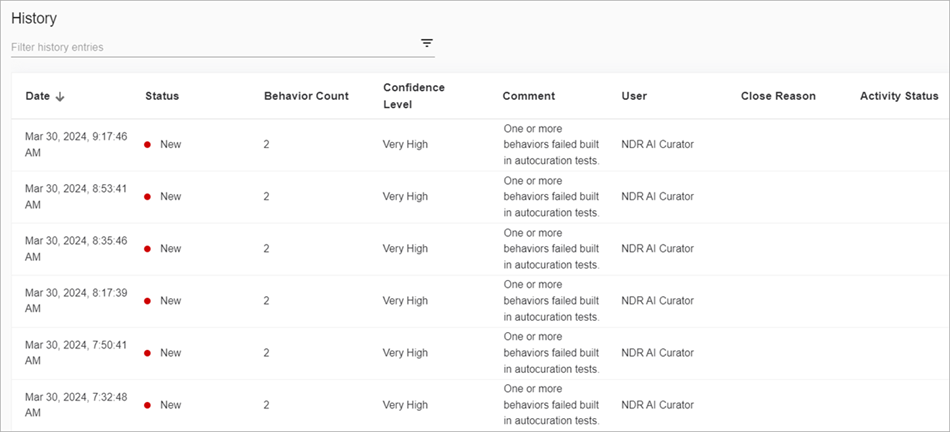
- Activity — Shows the history of the behavior and includes the behavior count, confidence, status, and user information.
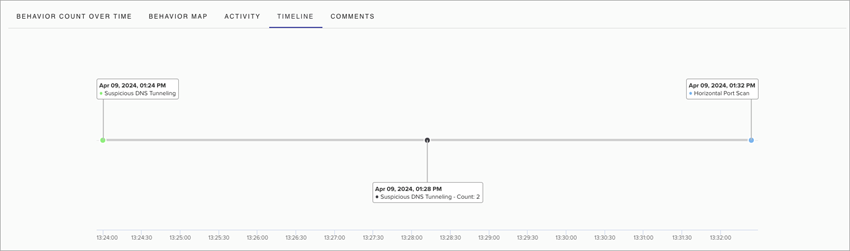
- Timeline — Shows the order in which behaviors occurred.
-
Comments — Shows any comments added by operators to the Smart Alert. When you review Smart Alerts, you can add comments to document Smart Alert activity and to communicate with other operators. To add a comment to a Smart Alert, click Comment.
Behavior Details
Every Smart Alert includes a list of behavior details. To view more detailed information about a specific behavior in the side pane, click ![]() next to the selected behavior.
next to the selected behavior.
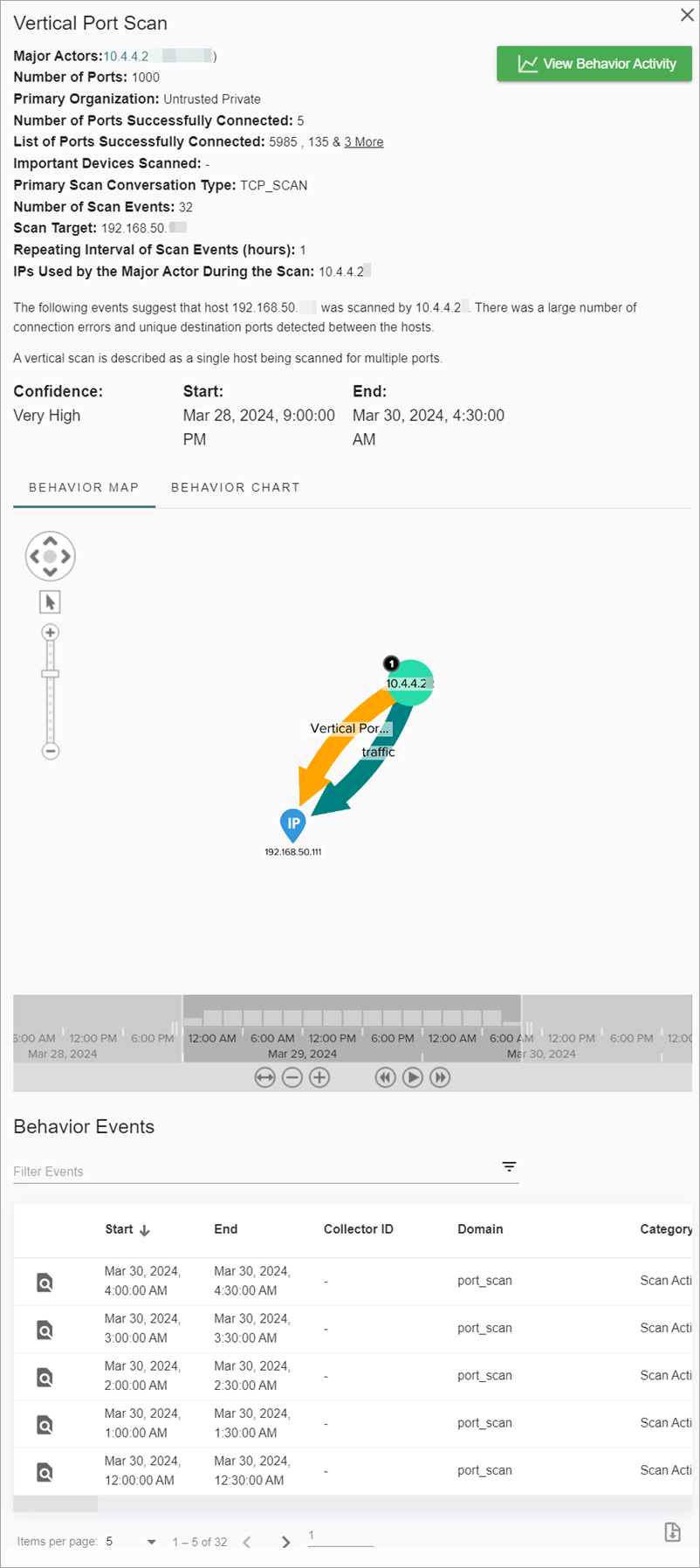
The side pane shows behavior maps and charts that detail the behavior for a specific time period. Behavior details vary by behavior type.
For example, details about a Suspicious DNS Tunneling behavior type include:
- Major Actors
- Important Devices Tunneled
- Major Suspected Tunnel Type
- Destination Organization
- Total Bytes Through Tunnel
- Destination Host
To interact with behavior maps and view further details, point to or click different sections of the map.
Remediate Smart Alerts
As you review Smart Alerts detected by ThreatSync+ NDR and review Smart Alert details, you can decide what actions to take on the threat. If the Smart Alert is a true threat, we recommend you follow the recommendations in the What to Look For section to address the threat.
If the threat originates outside of your network, consider the use of your firewall to block it. If the threat originates inside your network, identify the affected devices and physically remove them from the network. If a device is compromised, it is crucial you do not enable it to infect or attack other devices.
If you determine that the activity is authorized or harmless, you can close the Smart Alert and instruct ThreatSync+ NDR not to notify you about similar activity in the future. For more information, go to Close a Smart Alert.
Close a Smart Alert
It is important to close a Smart Alert after you review and remediate. This enables you to more easily keep track of open Smart Alerts and also enables ThreatSync+ NDR to track how quickly you complete the review and remediation process. Because ThreatSync+ NDR continuously learns your network, when you close Smart Alerts, you provide valuable feedback that helps the ThreatSync+ NDR AI to better understand your network and interpret future Smart Alerts.
We recommend you set up and configure the Executive Summary Report to view metrics of how many Smart Alerts are open for a specific time period, and how quickly operators address them. For more information, go to ThreatSync+ NDR Executive Summary Report.
When you close a Smart Alert, select from these reasons:
- Abnormal and Unauthorized — ThreatSync+ NDR correctly identified abnormal activity and this activity is not authorized on your network. You do not recognize the activity as part of your authorized business activity.
- Abnormal but Authorized — ThreatSync+ NDR correctly identified abnormal activity but you understand the source of the activity and know that it is authorized on the network. This might include activity such as authorized penetration tests or port scans.
- Normal Activity — This activity is expected on the network. When you close these Smart Alerts, you can specify that ThreatSync+ NDR must suppress future alerts. For example, this could be normal application activity such as network device scans or automated activity from authorized bots that might look like a tunnel.
- Other — You do not know what the Smart Alert is. It might be a threat but you cannot determine the root cause. When you close these Smart Alerts, you can provide more detail so that ThreatSync+ NDR can better understand whether this is a threat or not.
Avoid Repeated Smart Alerts for Authorized Activity
When you close a Smart Alert, ThreatSync+ NDR might ask other questions to learn from your actions. Your responses can help to reduce the number of non-threat alerts you receive.
To reduce the number of Smart Alerts that are false positives, select the Ignore Similar Smart Alerts check box when you close a Smart Alert. This creates a rule that shows on the Smart Alert Controls page. For more information, go to Configure ThreatSync+ NDR Smart Alert Controls.
To further control the similarities used to select the Smart Alerts you want to ignore, select Show more advanced options and specify specific properties.
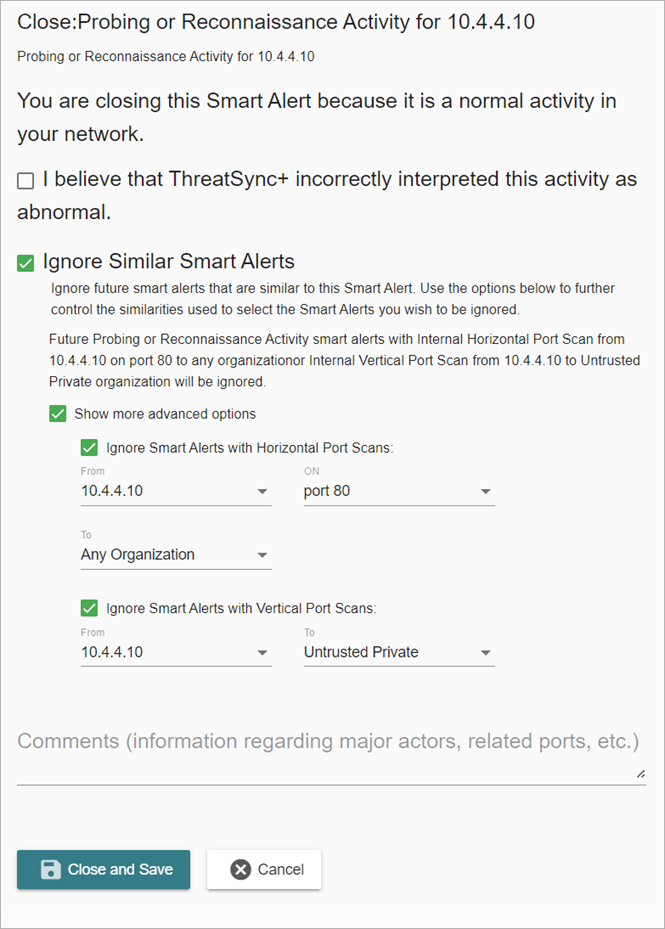
When you select the Ignore Similar Smart Alerts check box, ThreatSync+ NDR:
- Closes any open Smart Alerts with the same properties.
- Closes future Smart Alerts with the same properties that are detected before you are notified.
- Closes future Smart Alerts with the properties you specify in the advanced options section.