Applies To: ThreatSync+ NDR
To gain visibility into your network, you can monitor IP traffic across all the devices in your network.
Cloud-managed and locally-managed Fireboxes with cloud reporting that run Fireware v12.10.3 and higher automatically send network traffic data to WatchGuard Cloud and ThreatSync+ NDR. This data feed provides the information required for ThreatSync+ NDR to identify and detect potential threats and suspicious activities, such as lateral movements, DNS tunnels, fast and slow scans, and data exfiltration.
For locally-managed Fireboxes with cloud reporting, you must enable the Firebox to send log messages for reports in each policy. For more information, go to Set Logging and Notification Preferences in Fireware Help.
For Fireboxes that run lower versions of Fireware, third-party firewalls, or switches, you can use on-premise Windows or Linux-based collection devices called collectors to monitor network traffic. Collectors take data feeds such as NetFlow, sFlow, or Windows DHCP server logs directly from third-party switches and firewalls, and forward them through a secure connection to WatchGuard Cloud. These data feeds include information on the traffic that flows through the switch or firewall to network devices.
About Collection Agents for ThreatSync+ NDR
To install and configure collectors on computers and servers, you must first download and install the WatchGuard Agent and then configure the collectors for ThreatSync+ NDR.
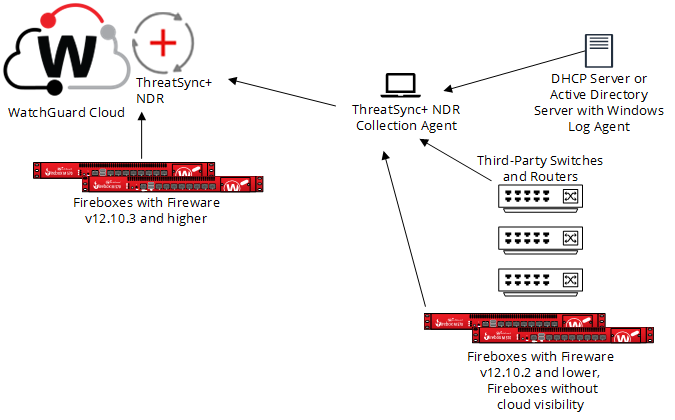
The ThreatSync+ NDR Collection Agent receives log data from switches and routers in your network, DHCP data from the Windows Log Agent, and data from locally-managed Fireboxes and sends the data to WatchGuard Cloud.
The ThreatSync+ NDR Collection Agent listens on:
- Port 2055 for NetFlow log data from endpoints.
- Port 6343 for sFlow log data from endpoints.
- Port 514 for DHCP log data from the Windows Log Agent.
ThreatSync+ NDR Collection Agent for Windows
You can install the ThreatSync+ NDR Collection Agent on Windows computers that run Windows 10, Windows 11, or Windows Server 2022.
To install and configure the WatchGuard Agent and the ThreatSync+ NDR Collection Agent for Windows, go to Configure Collectors for ThreatSync+ NDR (Windows Computers).
ThreatSync+ NDR Collection Agent for Linux
You can install the ThreatSync+ NDR Collection Agent on Linux computers that run Ubuntu 22.04 Server LTS or 24.04 Server LTS.
To install and configure the WatchGuard Agent and the ThreatSync+ NDR Collection Agent for Linux, go to Configure Collectors for ThreatSync+ NDR (Linux Computers).
Windows Log Agent
The Windows Log Agent is a collection agent that reads Windows DHCP server logs and then forwards them to the ThreatSync+ NDR Collection Agent. The ThreatSync+ NDR Collection Agent then forwards the DHCP logs to WatchGuard Cloud.
You can install the Windows Log Agent on Windows Server 2019 or 2022. Some of these servers could also be domain controllers.
To keep track of devices when they change their IP address, we recommend that you use the Windows Log Agent to collect Active Directory DHCP logs. Add and configure the Windows Log Agent on all DHCP servers.
To install and configure the Windows Log Agent, go to Configure the Windows Log Agent.
Quick Start — Set Up ThreatSync+ NDR