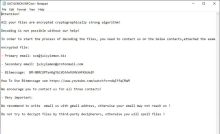
JuicyLemon is known to have debuted in mid-2016 when a user in the BleepingComputer's forums reported that their files had been encrypted. With the help of ransomware researchers, they revealed that the ransomware that infected this user's machine - along with a few others - is JuicyLemon. The name is derived from one of the emails the ransomware operators used to extort victims - support@juicylemon[.]biz. They also used another email for extortions as well as the Bitmessage service. These communication mediums were also used as strings in the abnormally long file extension the operators used after encrypting files with AES-256. Thankfully, a user in the same BleepingComputer's Forums named BloodDolly created a decryptor for JuicyLemon and any of its successors. One of which is PizzaCrypts, in which the decryptor works on it too. Public technical analyses of this ransomware show that the operators used exploit kits (EKs) to deliver their payloads. Specifically, they're known to have used the Angler and Neutrino EKs. Aside from that, the JuicyLemon operators are known to have asked for 1000 Euro as an extortion amount, but the currency they prefer is Bitcoin (BTC).
Ransomware - JuicyLemon
JuicyLemon
Description
Ransomware Type
Crypto-Ransomware
First Seen
Last Seen
Extortion Types
Direct Extortion
Extortion Amounts
Amount
1000EUR
Communication
Medio
Identificativo
Email
Email
Bitmessage
BM-NBRCUPTenKgYbLVCAfeVUHVsHFK6Ue2F
Encryption
Type
Symmetric
Files
AES-256
File Extension
<file name>.id-<10-digit victim ID>_
<file name>.id-<10-digit victim ID>[email protected]
<file name>.id-<10-digit victim ID>_email1_support_@_juicylemon.biz_email2_provectus_@_protonmail.com_BitMessage_BM-NBRCUPTenKgYbLVCAfeVUHVsHFK6Ue2F
Ransom Note Name
<Victim ID>.txt
JUICYLEMON INFO.txt
Read me now !.txt
RESTORE FILES.txt
Samples (SHA-256)
6a03fe836a9bf0ae9781623b273831d63ef87019d438e6b540ce5f2ee886f1b1
77eb59b2638936db2c0cdf8f46d64856ea886f98c17f3cc16200109f16f7f5f3
8afcaec180d4a4f29aac7b80f36848ff6eec08a5dabf2c3d86d205cc4da5c448
References & Publications
BlackBerry: Cylance vs. JuicyLemon Ransomware
BleepingComputer Forums: JuicyLemon Ransomware Help & Support Topic ([email protected])
Elastio: JuicyLemon
NJCCIC: JuicyLemon
PCrisk: JuicyLemon