Zeoticus 2.0 is the second iteration of the Zeoticus ransomware (obviously). These two variants share most of the same capabilities and is created by the same threat actor. At a high-level, the differences are minor. Here are a few examples of the similarities and differences:
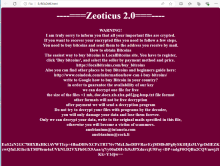
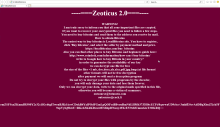
- Both iterations change the wallpaper background. However, Zeoticus 2.0 provides instructions on how to decrypt files. Whereas Zeoticus changes the wallpaper instructing users to go to the README file for further instructions.
- Zeoticus 2.0 can perform operations while being offline, while Zeoticus can't perform fully without Internet access.
- Both use XChaCha20 to encrypt files and curve25519xsalsa20poly1305 for asymmetric operations such as signing and encrypting the key.
- Both use HTML files for the ransom note.
- Both have long file extensions after encryption including the communication email address and a unique appending extension.
There are other differences, which were publicly posted by the threat actor on the XSS forum. Most of these are efficiency and speed related, but include changes to encrypt remote drives, including reconnecting to these drives if they are not connected. So, ensure you have password-protected network drives!
The BleepingComputer Forums had an individual admit they paid 1 BTC to decrypt their files, which they admit actually worked for them. At the time of that admission, BTC was between $13,000 and $14,000 dollars. To get this extortion amount, we take the high and low values of BTC on the day of the extortion (EST), take the average (divide by two), and then round to the nearest whole dollar.
Communication(8)
| Industry Sector | Country | Extortion Date | Amount (USD) |
|---|---|---|---|
| Individual | Unknown | ||
| Individual | Unknown | 1 BTC($13,526) |