Shift from Security Management to Security Operations
The advanced version of WatchGuard EPDR provides all the capabilities you’ll find in our standard EPDR, but with additional features to proactively search for compromised endpoints or harden them against the most common malwareless attack techniques. Combined with the cross-product correlation our Unified Security Platform architecture provides, Advanced EPDR heightens security efficacy against sophisticated attacks.
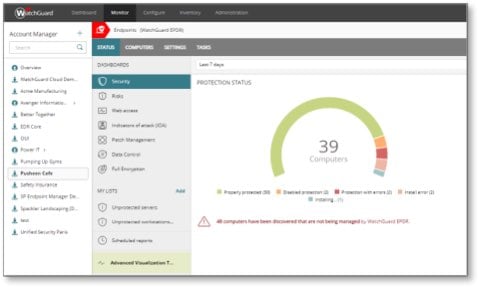
Close Security Gaps, Stay Ahead of Threats
Today's threat techniques are highly sophisticated and continuously evolving. Simple yet efficient hygiene practices can mean the difference between a minor security operation and becoming a victim. These practices range from reducing the attack surface of the endpoints to uncovering emerging campaigns lurking on the network before an actual compromise.
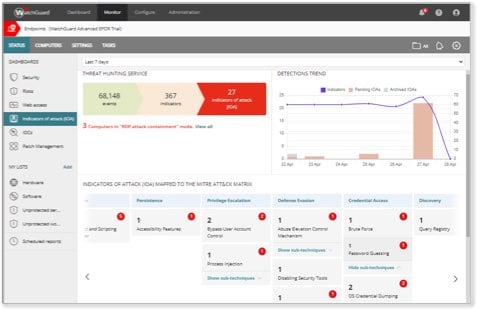
Threat Hunting and Suspicious Behavior Detection
Elevate your threat hunting capabilities by accessing deep endpoint telemetry, which allows you to search for suspicious behaviors proactively from a single Cloud-based console. With WatchGuard Advanced EPDR, your security team can continuously monitor endpoint activity, empowering them to detect and investigate even the most subtle signs of potential breaches, ensuring no threat goes unnoticed.
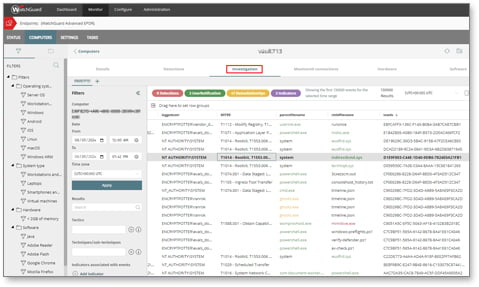
Advanced Endpoint Telemetry and MITRE ATT&CK Mapping
Security analysts gain access to enriched telemetry, including IoAs, extended events, CAPA tool insights, threat intelligence, and attack graphs. All this data is meticulously mapped to the MITRE ATT&CK framework, enabling rapid correlation and deep dives into attack tactics and techniques. This enhanced visibility supports swift and precise investigations and responses to security incidents.
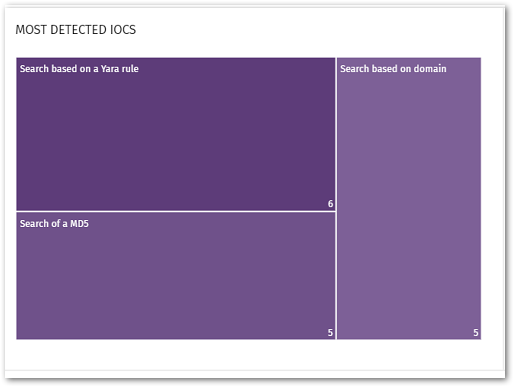
Centralize IoC-Based Hunting
WatchGuard Advanced EPDR offers a simple way to centrally manage and search for IoCs on the endpoints while consolidating the results in an intuitive dashboard. It enables your team to quickly hunt for recently disclosed incidents or exchange of security intelligence in your industry as well as find impacted endpoints in a forensic analysis. Different types of indicators are supported – hashes, filename, path, domain, IP, and Yara rules.
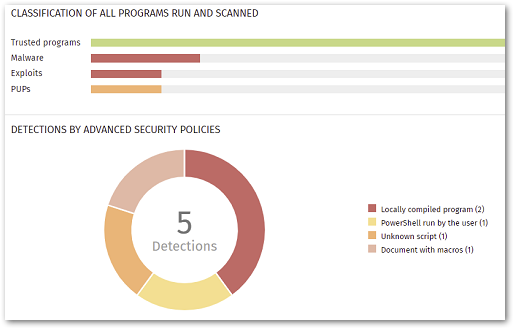
Monitor or Block Living-off-the-Land Attacks
The enhanced security policies enable you to supervise or harden endpoints from the execution of suspicious scripts and common attack techniques utilized by sophisticated threats such as:
- PowerShell with obfuscated parameters
- Unknown scripts
- Locally compiled programs
- Documents with macros
- Registry modifications that run when Windows starts
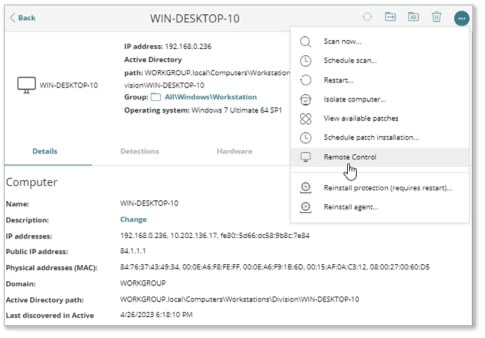
Remotely Investigate and Remediate an Incident
Real-Time Remote Shell is a powerful tool that allows you to access endpoints from the Cloud console, without requiring physical access to the endpoints for investigation, containment, and remediation actions including command line operations to manage processes and services, and transfer files, scripts, etc.
Compare WatchGuard EDR, EPDR, and Advanced EPDR
WatchGuard Advanced EPDR enables you to adopt a more proactive security stance, stay ahead of potential cyber threats, and strengthen your security program by adopting a more proactive posture with advanced capabilities on top of WatchGuard EPDR
| WatchGuard EDR |
WatchGuard EPDR |
WatchGuard Advanced EPDR |
|
|---|---|---|---|
| Proactive endpoint security within WatchGuard’s Unified Security Platform architecture | ✓ | ✓ | ✓ |
| Lightweight Cloud-based agent | ✓ | ✓ | ✓ |
| Zero-Trust Application Service: pre-execution, execution, and post-execution | ✓ | ✓ | ✓ |
| In-memory behavior anti-exploits | ✓ | ✓ | ✓ |
| Endpoints Risk Monitoring | ✓ | ✓ | ✓ |
| Threat Hunting Service: Behavior analytics – high fidelity IoA detection mapped to MITRE ATT&CK | ✓ | ✓ | ✓ |
| Persistent malware detections. Collective Intelligence lookups in real time | ✓ | ✓ | |
| IDS, firewall, and device control | ✓ | ✓ | |
| Web browsing protection and category-based URL filtering | ✓ | ✓ | |
| STIX and YARA rules IoCs search at the endpoints | ✓ | ||
| Threat Hunting Service: Behavior analytics – Non-deterministic IoA detection mapped to MITRE ATT&CK | ✓ | ||
| Contextual telemetry that allows non-deterministic IoA investigation | ✓ | ||
| Advanced security policies to reduce the attack surface | ✓ | ||
| Remote Shell from the Cloud: Click, connect, and manage endpoint processes, services, misconfigurations, files, and more | ✓ |
Ready to Unleash the True Power of WatchGuard Endpoint Security?
Delve into our products and unlock their full potential to take your cybersecurity program to the next level!
Explore Endpoint Security Solutions for Business
According to a Gartner® report, "Consolidation reduces the need for specialized skills, improves operational efficiencies and the efficacy of the security solutions. Tools that offer integrated security controls deliver more capabilities without adding more vendors, procurement, contracts, support, maintenance costs.”
Gartner, Quick Answer: How Can Midsize Enterprises Benefit From Security Vendor Consolidation? Published 3 March 2023, By Analyst Albert Gauthier
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved









