MSPs – the main victims of the Kaseya ransomware attack
In July, VSA, the remote working software of Kaseya, suffered one of the biggest ransomware incidents of 2021. Moreover, the main victims of this supply chain cyberattack were MSPs and the hackers demanded a higher ransom for this reason. What we know so far is it was a joint attack that affected between 1,500 and 2,000 organizations on the morning of July 2. Some of the companies, such as the Swedish supermarket chain Coop, were forced to interrupt their business and 11 schools in New Zealand were also hit.
The attack seems to have been launched by the REVIL group. They asked for a combined $70 million in exchange for the tool to decrypt the infected systems: for end customers the amount was $44,999, but MSPs received a demand for $5 million. This cyberattack also bears similarities to a hit the same group perpetrated against the hardware company ACER in March, which we covered previously in Secplicity. Thus far there have been no indications that the hackers managed to exfiltrate data and simply blocked the systems in exchange for the ransom. But how did this cyberattack happen?
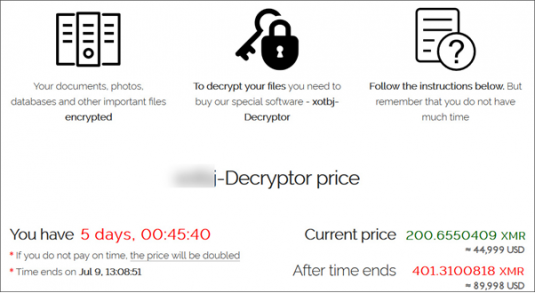
Ransom demand received by Kaseya victims
Zero Day Vulnerabilities
What we know at this stage is that REVIL exploited zero day vulnerabilities present in Kaseya's on-premises servers. Researchers from the Dutch DIVD Institute had already discovered these vulnerabilities so they were not completely unknown. However, Kaseya was still validating the patches for them at the time of the cyberattack.
DIVD and other analysts also conclude that the intruders used living-off-the-land techniques to bypass Kaseya authentication and inject SQL code to introduce the "agent.exe" malware containing the encryptor file.
Cybersecurity at multiple levels
As of August 4, Kaseya has announced the latest version of its VSA patch (VSA 9.5.7d) that it will start deploying on its SaaS servers as of Friday, August 6. In addition, a few days ago, the company also obtained a decryptor tool that unlocks infected systems and has made it available to customers affected.
Thanks to these efforts by Kaseya and other organizations, most of the companies targeted will have resolved this incident by now. But the cyberattack highlights the major threats MSPs face today. For these reasons, they need to be prepared with a multi-layered cybersecurity strategy: one type of protection is not enough because, as REVIL has shown, advanced threats employ multiple attack vectors.
Ideally, this requires a combination of MFA tools to ensure proper authentication, advanced network security and comprehensive Endpoint Detection and Response (EDR). Watchguard offers effective solutions for all of these areas. In fact, both our EPP/EDR software and network protection through Firebox detected and blocked the Kaseya malware.
But these solutions are enhanced when they work together: WatchGuard's Threat Detection and Response (TDR) is a powerful combination of tools against advanced malware that correlate with the threat indicators of Firebox devices at all times. Thus, it integrates network events and potential threats with full protection for endpoints. In addition, it includes the Host Ransomware Prevention (HRP) module, which automatically intervenes to stop ransomware before it blocks systems. This enables MSPs to minimize the risk of suffering incidents such as REVIL’s attack on Kaseya.


