Applies To: WatchGuard Cloud-managed Access Points (AP130, AP230W, AP330, AP332CR, AP430CR, AP432)
You can configure the wireless SSIDs that are broadcast by your access points and enable wireless clients to connect to your network.
Access points can have two different types of settings:
- Device-level settings that you apply individually to each access point — For more information, go to Configure SSID Settings for an Access Point.
- Settings that are applied to the access point from an Access Point Site — You can use Access Point Sites to create SSID settings that are applied to multiple access points that subscribe to the site. For more information, go to Configure SSID Settings for an Access Point Site.
Changes to SSID settings require the access point radios to restart to apply the new configuration. During this time, wireless clients will be temporarily disconnected as the new SSID settings are deployed.
Configure SSID Settings for an Access Point
To configure device-level SSID settings in WatchGuard Cloud for an access point:
- Select Configure > Devices.
- Select the access point you want to configure.
- Select Device Configuration.
The device configuration page opens.
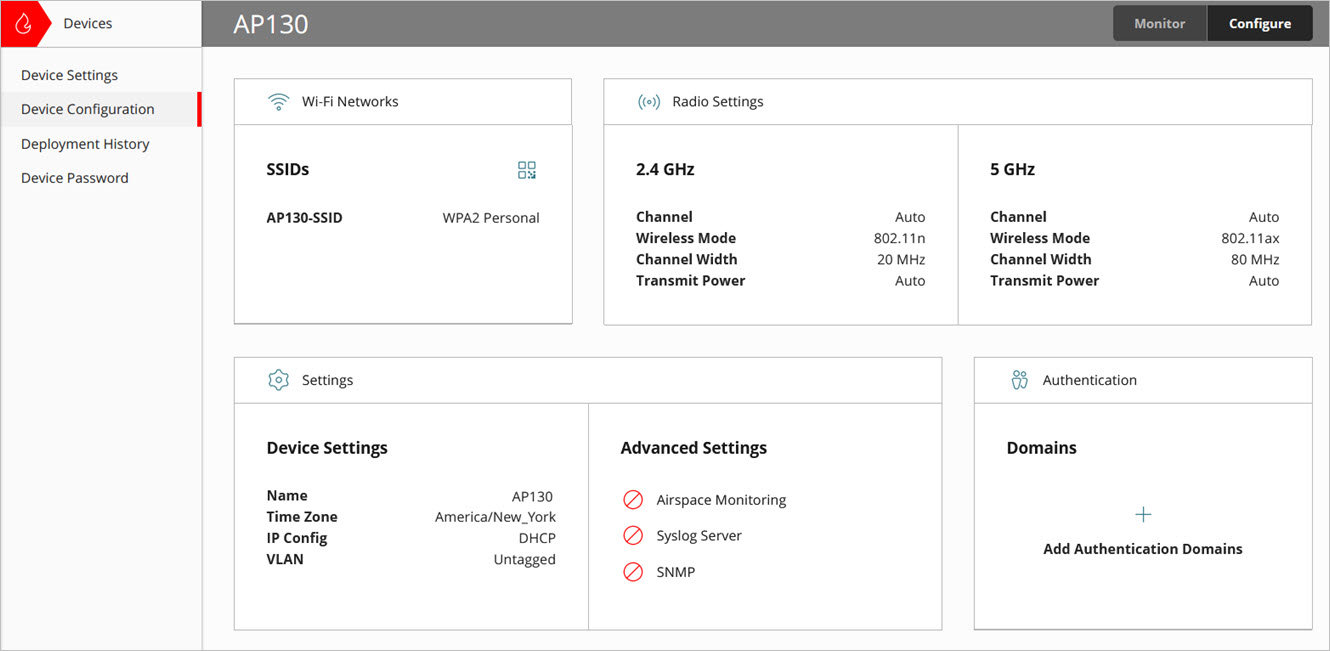
- In the Wi-Fi Networks tile, click SSIDs.
Configure SSID Settings for an Access Point Site
To configure SSID settings in WatchGuard Cloud for an Access Point Site:
- Select Configure > Access Points Sites.
- Select an existing site, or add a new site.
- From the Configuration Details tab, in the Wi-Fi Networks tile, click SSIDs.

Manage SSIDs
The SSIDs page lists your configured Wi-Fi networks and includes this information:

- SSID Name — The name of the Wi-Fi network SSID. There are two types of SSIDs, a device-level SSID, or an SSID configured from an Access Point Site, indicated by
 . From this page you can only add or delete device-level SSIDs. For more information about Access Point Sites, go to About Access Point Sites.
. From this page you can only add or delete device-level SSIDs. For more information about Access Point Sites, go to About Access Point Sites. - Broadcast — Indicates whether the SSID name is broadcast and visible to Wi-Fi clients.
- Security — The security type configured on this network, such as WPA2 Personal, WPA3 Personal, or Open.
- Radios — The access point radios that broadcast this SSID.
Add or Edit an SSID
To add a new SSID, click ![]() , or click an existing SSID name to edit the wireless network settings. For more information about the configuration settings for an SSID, go to SSID Settings.
, or click an existing SSID name to edit the wireless network settings. For more information about the configuration settings for an SSID, go to SSID Settings.
Delete an SSID
To delete an SSID, click ![]() then select Delete.
then select Delete.
SSID Settings
To add an SSID, click ![]() .
.
On each tab, you can configure different settings for the SSID such as wireless settings, access control, scheduling, traffic shaping, and advanced settings.
When you are finished your wireless network configuration, click Add to save the SSID.
Make sure you deploy your configuration changes to your access point after you save the configuration. For more information, go to Manage Device Configuration Deployment and Access Point Deployment History.
On the Wireless tab, you can configure the SSID name, specify if the network is private or for guests, specify the radios to broadcast the SSID, enable SSID security, edit and create an SSID QR code voucher, download an SSID QR Code, and configure network settings.

- SSID Name — Type the SSID name. This is the name for this wireless network that appears to clients.
- Broadcast SSID — Select the Broadcast SSID check box to broadcast the SSID name to wireless clients. Clear this check box if you want to hide the SSID name.
- SSID Type
- Private — Create a private wireless network.
- Guest — Create a guest wireless network that provides limited access to protect devices and resources on your private wireless network. When you select a Guest network, Client Isolation is also enabled by default. For more information, go to Client Isolation.
To apply different IP address ranges to your wireless networks, you can configure the SSID in NAT mode in the Network section.
- Radio — Select the access point radios (2.4 GHz, 5 GHz, or both 2.4 GHz and 5 GHz) that broadcast this SSID.
- Security — Select the type of security for this SSID.
- Open — Open means no security encryption is applied. This option is typically used for public guest networks.
- OWE — Opportunistic Wireless Encryption (OWE), also known as Enhanced Open, is the latest and most secure open protocol for Wi-Fi 6 (802.11ax) access points that provides each user with encryption that protects data exchange between the client and the wireless network. This enables you to create an open network that provides data privacy without authentication. Clients that do not support OWE cannot connect with an SSID configured with OWE. Both the access point and client must support OWE.
- WPA2 Personal (default) — WPA2 is the latest and most secure protocol for 802.11a/b/g/n/ac access points. You must type a Passphrase that wireless users must use to connect to this SSID.
- WPA3/WPA2 — A mixed mode of WPA3 and WPA2 protocols. You must type a Passphrase that wireless users must use to connect to this SSID.
- WPA3 Personal — WPA3 is the latest and most secure protocol for Wi-Fi 6 (802.11ax) devices. WPA3 enables Protected Management Frames (802.11w) for higher security. Wireless clients must also support 802.11ax to use WPA3. You must type a Passphrase that wireless users must use to connect to this SSID.
- Passphrase — If you selected a security method that uses a pre-shared key such as WPA2 Personal or WPA3 Personal, type the passphrase to use. Wireless users must specify this passphrase when they connect to the SSID.
There is an open issue where wireless clients with older operating systems that do not support WPA3 are unable to connect to an SSID with mixed WPA3/WPA2 security. For more information, go to the WatchGuard Knowledge Base.
- WPA2 Enterprise — The WPA2 protocol with enterprise RADIUS authentication. In access point firmware v2.1 and higher, you can customize the Called Station ID and NAS ID RADIUS attributes in the advanced settings of an SSID. For more information, go to Configure RADIUS Authentication for an Access Point.
- WPA3 Enterprise — The WPA3 protocol with enterprise RADIUS authentication. With WPA3 Enterprise, you can also enable 192-bit mode (WPA3 Enterprise Suite B) to increase encryption security in sensitive enterprise environments. WPA3 Enterprise 192-bit mode requires access point firmware v2.1 or higher. In access point firmware v2.1 and higher, you can customize the Called Station ID and NAS ID RADIUS attributes in the advanced settings of an SSID. For more information, go to Configure RADIUS Authentication for an Access Point.
- Authentication Domain — If you selected the WPA2 Enterprise or WPA3 Enterprise security mode, you must select an authentication domain with your configured RADIUS servers from the drop-down list. For more information, go to Access Point Authentication Domains. If there are no Authentication Domains configured, you must add an authentication domain in Configure > Shared Configurations > Authentication Domains.
- For more information, go to Access Point Authentication Domains.
- For more information about how to use RADIUS to authenticate wireless clients, go to Configure RADIUS Authentication for an Access Point.
SSID QR Code
You can generate and print a QR code that enables wireless users to easily connect to an access point SSID. For more information, go to Configure Access Point SSID QR Code.
In the Network section, you can configure network settings for your SSID.
- Enable VLAN — Enables you to map your wireless network SSID to a VLAN ID on your network. You can manually assign a VLAN ID from 1 to 4094 for each SSID. For example, you can configure VLANs to separate network traffic between your SSIDs, such as private and guest SSIDs. For more information on VLANs and your wireless networks, go to Access Points and VLANs.
These VLAN options appear if you configure WPA2 or WPA3 Enterprise security for the SSID: - Untagged VLAN — The SSID is configured as an untagged VLAN. No tagged VLAN ID is assigned. This is the default setting.
- Dynamic VLAN assigned by RADIUS — Enable Dynamic VLAN assignment for a wireless client. The VLAN assigned to the client is based on the user information provided by the RADIUS server after successful authentication.
If no VLAN attribute is returned from the RADIUS server for the user, from the Unassigned RADIUS clients drop-down list, you can assign the VLAN as untagged, or as the VLAN you manually configure for the SSID. For more information, go to Configure Access Point Dynamic VLANs. - VLAN assigned by SSID — You can manually assign a VLAN ID from 1 to 4094 for each SSID.
- Bridged (default) — Use a bridged network when the access point and the clients associating with the access point are in the same subnet.
- NAT — Use Network Address Translation (NAT) when you want to have the clients and the access point in a separate subnet. Wireless clients use a private IP address pool assigned from the access point.
- You cannot use NAT at the same time as Dynamic VLANs. For more information, go to Configure Access Point Dynamic VLANs.
- You must enable NAT to use this SSID with an access point VPN. For more information, go to Configure an Access Point VPN.
- Fast Roaming is disabled if you use NAT.
You must configure these settings when you enable NAT:
- Local IP Address (Gateway) — An IP address in the selected network outside of the DHCP address pool. This address is used as the gateway address for the clients on the wireless network.
- Subnet Mask — The net mask for the selected network.
- DHCP Pool Start IP Address — The starting IP address of the DHCP address pool in the selected network.
- DHCP Pool End IP Address — The end IP address of the DHCP address pool in the selected network.
- Lease Time — The DHCP lease time in hours (1 to 24).
- Primary and Secondary DNS Server — The primary and secondary DNS servers to which wireless clients make DNS queries.
To control access for specific wireless clients based on their MAC address, enable the MAC Address Access Control List.
- Use the Allowed MAC Address List to only allow access for the client MAC addresses that you specify.
- Use the Blocked MAC Address List to block wireless clients based on the MAC addresses that you specify.
To add a new address, click Add MAC Address. When you have finished, click Add to save the access control list.

The maximum number of MAC addresses supported depends on the firmware version of the access point.
- Access points that run firmware version 1.1.24 or higher support a maximum of 256 MAC addresses.
- Devices with firmware versions lower than 1.1.24 only support a maximum of 32 MAC addresses. Imported lists for these devices are truncated to 32 addresses.
Import MAC Address List
To upload a list of multiple MAC addresses, click Import MAC Address List.

You can drag and drop a MAC address list into the box or select the MAC address list file.
The MAC address list file must be in comma-separated value format (CSV), with a MAC address and an optional description.
For example, to import addresses with a description:
00:aa:00:bb:00:c1,Description
00:aa:00:bb:00:c2,Description
To import addresses with no description:
00:aa:00:bb:00:c1
00:aa:00:bb:00:c2
To import addresses with and without descriptions:
00:aa:00:bb:00:c1,Description
00:aa:00:bb:00:c2
00:aa:00:bb:00:c3,Description
00:aa:00:bb:00:c4
When the imported file is analyzed, you can select the MAC addresses to import. Click Save to import the MAC addresses.

Specify when to enable Wi-Fi access for this SSID. This limits access to this SSID based on the times you configure. For example, you might want to limit wireless guest access to only business hours. The times are based on a 24-hour clock with minimum 30-minute intervals.
The default is Always Available. You can also select a pre-configured schedule for 8:00AM to 5:00PM Monday to Friday, or create a Custom Schedule.
Access point VPNs configured with this SSID are also enabled and disabled by the configured SSID schedule. For more information, go to Configure an Access Point VPN.

You can enable bandwidth controls that limit the bandwidth usage on this SSID. For example, you can enable limits on your guest SSID so that guest users do not use too much bandwidth and affect wireless performance on your private wireless network.
To enable bandwidth controls, select SSID Bandwidth Control.
Specify the Upload Limit and Download Limit in Mbps. You can select a value from 1 to 999 Mbps.
These limits are applied to traffic on the entire SSID.
To apply these upload and download limits to each individual user on the SSID, select the corresponding Per Client check box.

Advanced options enable you to configure additional management, security, and steering options for this SSID.

- Protected Management Frames (802.11w) — For WPA2 and WPA3 security encryption, you can enable additional management frame protection to prevent spoofing attacks that use deauthentication and disassociation management frame actions. You can select Allow All Clients which only protects 802.11w-capable clients, or select Allow Only 802.11w Capable Clients. 802.11w is mandatory and enabled automatically for WPA3 encryption.
- Called Station ID/NAS ID — For WPA2 and WPA3 Enterprise authentication, you can customize RADIUS attributes that identify the access point and client to the RADIUS server during authentication. You can enter custom text in combination with the predefined variables. You must use the % character with a variable. The maximum length for the field is 32 characters. With variable expansion, the maximum length of the Called Station ID or NAS ID is 84 characters.
- %m — MAC address of the access point Ethernet interface
- %s — SSID name
- %n — Device name
This feature requires access point firmware v2.1 or higher. For more information, go to Configure RADIUS Authentication for an Access Point.

- Fast Roaming (802.11k/r) — When you select WPA2 Personal or WPA2 Enterprise security encryption, you can also enable Fast Roaming to reduce the re-authentication time for a wireless client as it roams from one WatchGuard access point to another access point. This enables the wireless client to quickly transition wireless communications and improves performance and stability of streaming-intensive applications such as VoIP and video streaming. Fast Roaming is primarily recommended for networks with WPA2 Enterprise to reduce RADIUS authentication times when roaming. Wireless clients must support the 802.11k and 802.11r standards to use Fast Roaming. In some cases, some older wireless clients have issues connecting to a network with Fast Roaming enabled. Fast Roaming is disabled if NAT is enabled on the SSID. Fast Roaming is enabled automatically with WPA3 security.
- Band Steering — Band steering actively steers wireless clients from the 2.4 GHz band to use the less congested 5 GHz band to help balance associated clients on an access point between the 2.4 GHz and 5 GHz radios. Band steering also enables 802.11v support to improve roaming behavior for clients and help them find better access points to associate with.

You can choose from these settings:
- Balance Clients: Distributes the wireless client load between the 2.4 GHz and 5 GHz radios. In the Balance Ratio text box, specify the percentage of clients that can use the 5 GHz radio. The remaining percentage must use the 2.4 GHz radio.
- Prefer 5 GHz (default): Clients are steered to the 5 GHz band if the client's signal strength in 5 GHz is higher than the configured RSSI Threshold (default -75 dBm).
- Force 5 GHz: Enables the use of additional management packets to make sure a client is always disconnected from the 2.4 GHz radio and steered to the 5 GHz radio when the client reconnects to the access point.
- Client Isolation — Prevents wireless clients from communicating directly to other wireless or wired clients and devices connected to the same network. Client isolation is useful in typical guest Wi-Fi access deployments to prevent communications between guest clients and other clients and devices on the network. Client isolation is enabled by default if the SSID is configured as a Guest SSID.
- Network Access Enforcement — Network Access Enforcement provides an extra layer of security when a wireless client connects to the corporate wireless network. Network Access Enforcement requires a wireless client to have a WatchGuard Endpoint Security product installed (WatchGuard Advanced EPDR, EPDR, EDR, EDR Core, or EPP) before the device can connect to the wireless network. Network Access Enforcement requires access point firmware v2.1 or higher. For more information, go to Access Point Network Access Enforcement.

Configure Access Point Device Settings